@prisma/security-rules 0.3.6 → 0.3.7
This diff represents the content of publicly available package versions that have been released to one of the supported registries. The information contained in this diff is provided for informational purposes only and reflects changes between package versions as they appear in their respective public registries.
- package/README.md +53 -63
- package/assets/rpc.png +0 -0
- package/dist/index.cjs +1 -1137
- package/dist/index.d.cts +20 -170
- package/dist/index.d.ts +20 -170
- package/dist/index.js +1 -1109
- package/package.json +2 -4
package/README.md
CHANGED
|
@@ -4,10 +4,10 @@
|
|
|
4
4
|
|
|
5
5
|
Prisma Security Rules is a **permission rules system for Prisma ORM and Prisma Postgres**. With Security Rules, you can:
|
|
6
6
|
|
|
7
|
-
-
|
|
8
|
-
-
|
|
9
|
-
-
|
|
10
|
-
-
|
|
7
|
+
- Define access permission rules in TypeScript
|
|
8
|
+
- Deploy the permission rules to your Prisma Postgres instance
|
|
9
|
+
- Query Prisma Postgres with the permission rules applied
|
|
10
|
+
- Access Prisma Postgres from the frontend
|
|
11
11
|
|
|
12
12
|
At the core of it, you define rules that allow/deny requests to your database based on model name, operation (e.g. `findMany`) and the parameters you pass to said operation.
|
|
13
13
|
|
|
@@ -15,11 +15,11 @@ At the core of it, you define rules that allow/deny requests to your database ba
|
|
|
15
15
|
|
|
16
16
|
### Prerequisites
|
|
17
17
|
|
|
18
|
-
- A project with Prisma ORM (>=6.2.0) installed and a Prisma Postgres database. If you don’t have one, you can get started [here](https://www.prisma.io/docs/getting-started/prisma-postgres/from-the-cli?utm_source=readme&utm_medium=
|
|
18
|
+
- A project with Prisma ORM (>=6.2.0) installed and a Prisma Postgres database. If you don’t have one, you can get started [here](https://www.prisma.io/docs/getting-started/prisma-postgres/from-the-cli?utm_source=readme&utm_medium=security_rules).
|
|
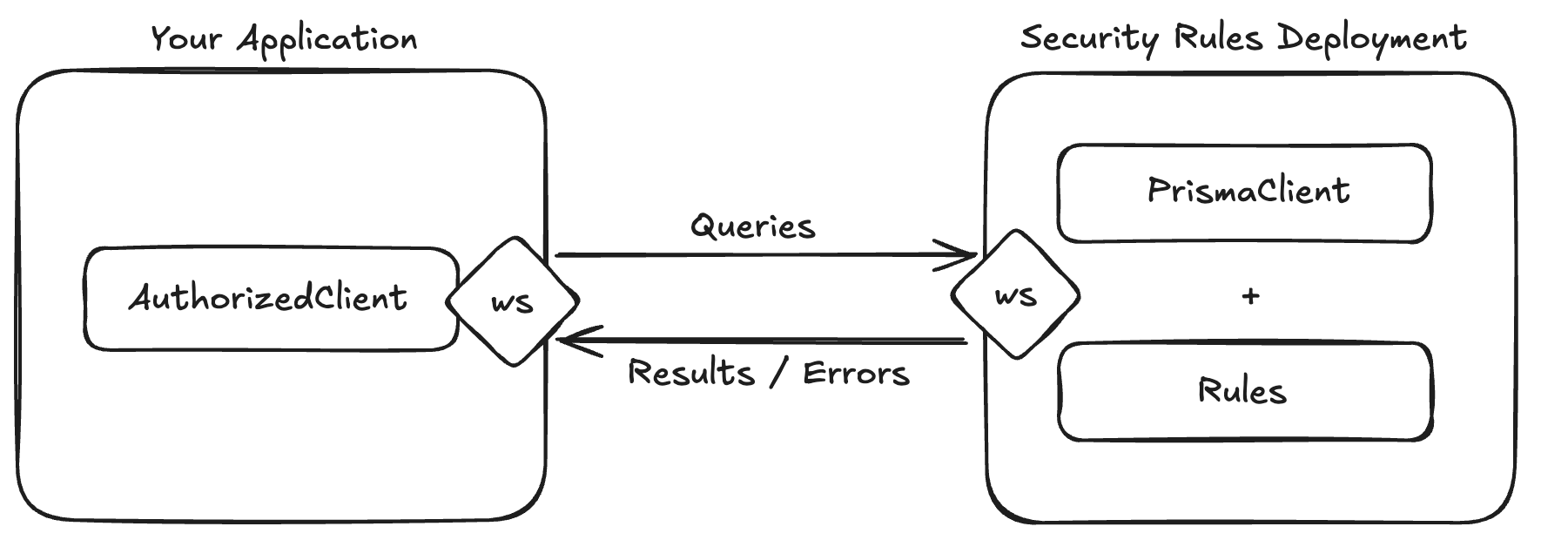
19
19
|
|
|
20
|
-
- The Prisma CLI being authenticated with Prisma Data Platform (via [`prisma platform auth login --early-access`](https://www.prisma.io/docs/platform/platform-cli/commands?utm_source=readme&utm_medium=
|
|
20
|
+
- The Prisma CLI being authenticated with Prisma Data Platform (via [`prisma platform auth login --early-access`](https://www.prisma.io/docs/platform/platform-cli/commands?utm_source=readme&utm_medium=security_rules#auth-login)).
|
|
21
21
|
|
|
22
|
-
### 1. Install the
|
|
22
|
+
### 1. Install the Security Rules package
|
|
23
23
|
|
|
24
24
|
```shell
|
|
25
25
|
npm install @prisma/security-rules
|
|
@@ -50,74 +50,67 @@ bun install @prisma/security-rules
|
|
|
50
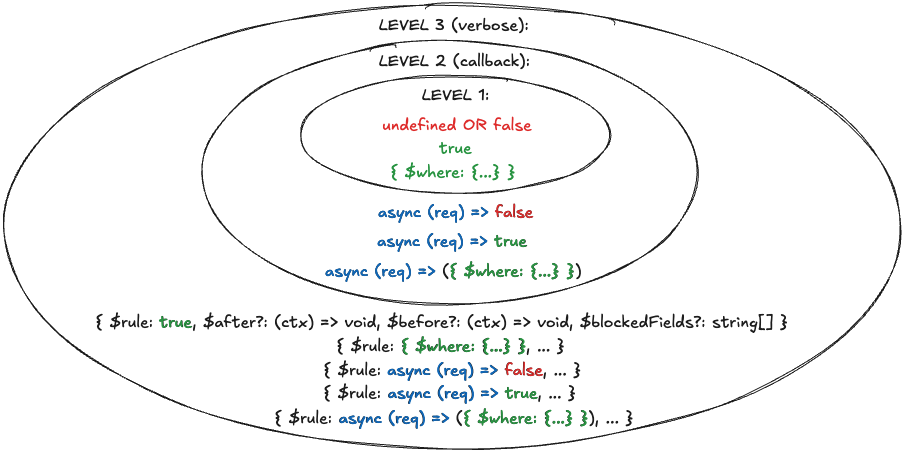
50
|
|
|
51
51
|
</details>
|
|
52
52
|
|
|
53
|
-
### 2.
|
|
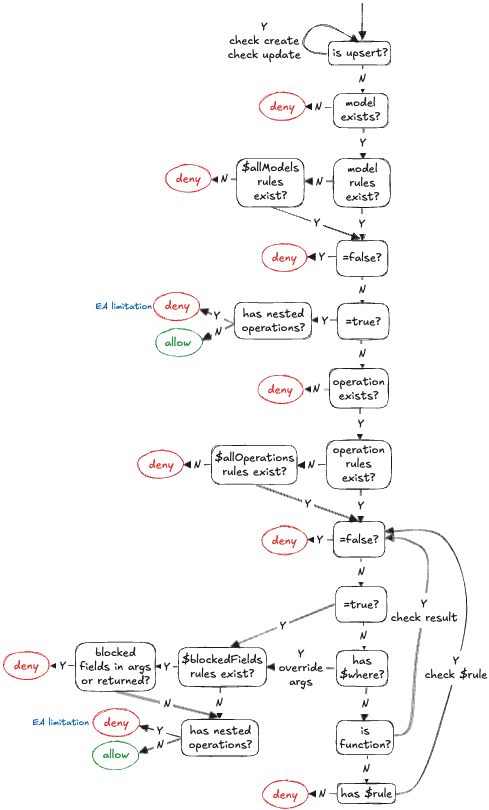
53
|
+
### 2. Define your Security Rules
|
|
54
54
|
|
|
55
|
-
First, import the
|
|
55
|
+
First, import the package and define your rules. Create a `rules.ts`in your `prisma` folder:
|
|
56
56
|
|
|
57
57
|
```ts
|
|
58
58
|
import { PrismaClient } from "@prisma/client";
|
|
59
|
-
import {
|
|
59
|
+
import { defineRules } from "@prisma/security-rules";
|
|
60
60
|
import { z } from "zod";
|
|
61
61
|
|
|
62
62
|
import { decode } from "path/to/decode"; // imaginary import of your jwt token decode helper
|
|
63
63
|
|
|
64
|
-
export
|
|
65
|
-
|
|
66
|
-
|
|
67
|
-
|
|
68
|
-
|
|
69
|
-
|
|
70
|
-
|
|
71
|
-
|
|
72
|
-
|
|
73
|
-
|
|
74
|
-
|
|
75
|
-
|
|
76
|
-
|
|
77
|
-
|
|
78
|
-
},
|
|
79
|
-
$allOperations: false,
|
|
64
|
+
export default defineRules({
|
|
65
|
+
prisma: new PrismaClient(),
|
|
66
|
+
contextSchema: z.object({
|
|
67
|
+
token: z.string(),
|
|
68
|
+
}),
|
|
69
|
+
rules: {
|
|
70
|
+
user: {
|
|
71
|
+
async read(req) {
|
|
72
|
+
// On each request, the context object can be used to perform custom auth/access business logic. We know it's shape thanks to the `contextSchema` property.
|
|
73
|
+
const { userId } = await decode(req.context.token);
|
|
74
|
+
|
|
75
|
+
return {
|
|
76
|
+
$where: { id: userId },
|
|
77
|
+
};
|
|
80
78
|
},
|
|
81
|
-
$
|
|
82
|
-
$transaction: false,
|
|
79
|
+
$allOperations: false,
|
|
83
80
|
},
|
|
84
|
-
|
|
85
|
-
|
|
81
|
+
$allModels: false,
|
|
82
|
+
$transaction: false,
|
|
83
|
+
},
|
|
84
|
+
});
|
|
86
85
|
```
|
|
87
86
|
|
|
88
87
|
> Note: While the rules are applied to your `PrismaClient` instance, this instance will retain _full_ database access.
|
|
89
88
|
|
|
90
89
|
This example uses `zod`, but you can use any schema library that implements the [standard schema](https://github.com/standard-schema/standard-schema#what-schema-libraries-implement-the-spec) specification.
|
|
91
90
|
|
|
92
|
-
This example includes
|
|
93
|
-
|
|
94
|
-
### 3. Create a file exporting the `PolicyClient` for your application
|
|
91
|
+
This example includes rules that will deny all requests except for reads (e.g. `findMany`) on `user` model. It also ensures a user only sees their own data by applying a `where` override (effectively `AND(incoming_query_where, rule_$where)`) that filters by the user's id (decoded from the session token).
|
|
95
92
|
|
|
96
|
-
|
|
97
|
-
import { PolicyClient } from "@prisma/security-rules";
|
|
98
|
-
|
|
99
|
-
// it is very important to not forget the `type` annotation here, to tell TypeScript to only import the types!!!
|
|
100
|
-
import type { prisma as rpcClient } from "path/to/file/where/rules/are/used";
|
|
101
|
-
|
|
102
|
-
export const prisma = new PolicyClient<typeof rpcClient>({
|
|
103
|
-
publicKey: "<TBD>",
|
|
104
|
-
});
|
|
105
|
-
```
|
|
106
|
-
|
|
107
|
-
### 4. Deploy Policy rules
|
|
93
|
+
### 3. Deploy your Security Rules
|
|
108
94
|
|
|
109
95
|
```shell
|
|
110
|
-
prisma rules deploy <rules_name> -f
|
|
96
|
+
prisma rules deploy <rules_name> -f ./prisma/rules.ts
|
|
111
97
|
```
|
|
112
98
|
|
|
113
|
-
Be sure to copy the public key from the deploy command's output in your terminal, and replace the `<
|
|
99
|
+
Be sure to copy the public key from the deploy command's output in your terminal, and replace the `<public_key>` below.
|
|
114
100
|
|
|
115
|
-
###
|
|
101
|
+
### 4. Use `AuthorizedClient` to access Prisma Postgres
|
|
116
102
|
|
|
117
|
-
`
|
|
103
|
+
`AuthorizedClient` is a lightweight version of `PrismaClient` that you can use in your browser. Once your rules are deployed, you can use it as follows in your application:
|
|
118
104
|
|
|
119
105
|
```ts
|
|
120
|
-
import {
|
|
106
|
+
import { AuthorizedClient } from "@prisma/security-rules";
|
|
107
|
+
|
|
108
|
+
// It is important not to forget the `type` annotation here.
|
|
109
|
+
import type rules from "./prisma/rules";
|
|
110
|
+
|
|
111
|
+
const authorizedClient = new AuthorizedClient<typeof rules>({
|
|
112
|
+
publicKey: "<public_key>",
|
|
113
|
+
});
|
|
121
114
|
|
|
122
115
|
prisma.setGlobalContext({ token: "<some_session_token>" });
|
|
123
116
|
|
|
@@ -128,23 +121,20 @@ const users = await prisma.users.findMany();
|
|
|
128
121
|
|
|
129
122
|
This package exposes:
|
|
130
123
|
|
|
131
|
-
- A
|
|
132
|
-
|
|
133
|
-
- A lightweight Remote Procedure Call (RPC) stub called `PolicyClient` that allows your application to execute Prisma ORM queries and transactions remotely on Prisma Policy's workers in a secure way (based on your Policy configuration).
|
|
124
|
+
- A `defineRules` helper to attach Prisma Security Rules to an existing Prisma ORM client, which gets deployed at the edge when you run `prisma rules deploy`.
|
|
134
125
|
|
|
135
|
-
|
|
126
|
+
- An `AuthorizedClient` class that is a drop-in replacement for `PrismaClient`, a lightweight client that will enforce the rules you've defined and deployed.
|
|
136
127
|
|
|
137
|
-
Here's a simplified high-level view of
|
|
128
|
+
Here's a simplified high-level view of Prisma Security Rule's architecture:
|
|
138
129
|
|
|
139
|
-
|
|
140
131
|
|
|
141
132
|
### Rule Engine
|
|
142
133
|
|
|
143
|
-
Each request, that is received by
|
|
144
|
-
|
|
145
|
-
- if a request does not adhere to your rules, it will be denied with a reason, and the `PolicyClient` will throw an error.
|
|
134
|
+
Each request, that is received by Prisma Security Rules' workers, will be evaluated by a rule engine:
|
|
146
135
|
|
|
147
|
-
-
|
|
136
|
+
- If a request does not adhere to your rules, it will be denied with a reason, and the `AuthorizedClient` will throw an error.
|
|
137
|
+
- If a request adheres to your rules, it will be executed with the `PrismaClient` and the results will be sent to the `AuthorizedClient`.
|
|
148
138
|
|
|
149
139
|
#### Rules
|
|
150
140
|
|
|
@@ -193,7 +183,7 @@ type ModelRules =
|
|
|
193
183
|
|
|
194
184
|
Operation rules are best described by the following diagram:
|
|
195
185
|
|
|
196
|
-
|
|
197
187
|
|
|
198
188
|
It's like an 🧅.
|
|
199
189
|
|
|
@@ -213,10 +203,10 @@ The callback's `req` argument is an object that includes the model name, operati
|
|
|
213
203
|
|
|
214
204
|
Here's a diagram depicting the rule engine's evaluation process in a simplified manner:
|
|
215
205
|
|
|
216
|
-
|
|
217
207
|
|
|
218
208
|
The rule engine is designed to introduce as little overhead as possible. As soon as a rule is not adhered by some check, the request is denied. Meaning, it doesn't try and run additional checks to collect more deny reasons.
|
|
219
209
|
|
|
220
210
|
## Need help?
|
|
221
211
|
|
|
222
|
-
If you need assistance, reach out in the #help-and-questions channel on our [Discord](https://pris.ly/discord), or connect with our community to see how others are using
|
|
212
|
+
If you need assistance, reach out in the #help-and-questions channel on our [Discord](https://pris.ly/discord), or connect with our community to see how others are using Prisma Security Rules.
|
package/assets/rpc.png
CHANGED
|
Binary file
|