smart_proxy_openscap 0.4.1 → 0.5.0
This diff represents the content of publicly available package versions that have been released to one of the supported registries. The information contained in this diff is provided for informational purposes only and reflects changes between package versions as they appear in their respective public registries.
- checksums.yaml +4 -4
- data/.rubocop.yml +41 -0
- data/.rubocop_todo.yml +111 -0
- data/Gemfile +8 -0
- data/README.md +58 -37
- data/Rakefile +14 -0
- data/bin/smart-proxy-openscap-send +1 -1
- data/lib/smart_proxy_openscap/fetch_scap_content.rb +58 -0
- data/lib/smart_proxy_openscap/foreman_forwarder.rb +38 -0
- data/lib/smart_proxy_openscap/openscap_api.rb +76 -17
- data/lib/smart_proxy_openscap/openscap_content_parser.rb +56 -0
- data/lib/smart_proxy_openscap/openscap_exception.rb +4 -17
- data/lib/smart_proxy_openscap/openscap_lib.rb +13 -169
- data/lib/smart_proxy_openscap/openscap_plugin.rb +3 -1
- data/lib/smart_proxy_openscap/openscap_report_parser.rb +93 -0
- data/lib/smart_proxy_openscap/openscap_version.rb +1 -1
- data/lib/smart_proxy_openscap/spool_forwarder.rb +64 -0
- data/lib/smart_proxy_openscap/storage.rb +45 -0
- data/lib/smart_proxy_openscap/storage_fs.rb +71 -0
- data/settings.d/openscap.yml.example +8 -0
- data/smart_proxy_openscap.gemspec +7 -1
- data/test/data/arf_report +0 -0
- data/test/data/ssg-rhel7-ds.xml +20271 -0
- data/test/fetch_scap_api_test.rb +71 -0
- data/test/get_report_xml_html_test.rb +52 -0
- data/test/post_report_api_test.rb +75 -0
- data/test/scap_content_parser_api_test.rb +54 -0
- data/test/test_helper.rb +11 -0
- metadata +93 -4
checksums.yaml
CHANGED
|
@@ -1,7 +1,7 @@
|
|
|
1
1
|
---
|
|
2
2
|
SHA1:
|
|
3
|
-
metadata.gz:
|
|
4
|
-
data.tar.gz:
|
|
3
|
+
metadata.gz: 52077a3d7e9a009b0ab9d8abba663b3ab7191b78
|
|
4
|
+
data.tar.gz: db0401879d67124ea9361d48800dad7a66675d37
|
|
5
5
|
SHA512:
|
|
6
|
-
metadata.gz:
|
|
7
|
-
data.tar.gz:
|
|
6
|
+
metadata.gz: 8133075f66c34e22e0da4c431dd49bcd4a3530f8fb8a2f8d7b564b3e781d06eb251ce4db830ad1d87a739d646d55427ec18a60ee06f196b3b318eb55a7a6ac36
|
|
7
|
+
data.tar.gz: 12d22393be694c5f68e3b3ce5fa48afc592c5baee07fab7c3c760e358755bb96d07f32e84eaaf4a4a238b432c3d41ac98994d16f906c7b08c63032b0d0a60e6d
|
data/.rubocop.yml
ADDED
|
@@ -0,0 +1,41 @@
|
|
|
1
|
+
inherit_from: .rubocop_todo.yml
|
|
2
|
+
|
|
3
|
+
# Offense count: 11
|
|
4
|
+
Lint/AmbiguousRegexpLiteral:
|
|
5
|
+
Enabled: false
|
|
6
|
+
|
|
7
|
+
# Offense count: 14
|
|
8
|
+
# Configuration parameters: AllowSafeAssignment.
|
|
9
|
+
Lint/AssignmentInCondition:
|
|
10
|
+
Enabled: false
|
|
11
|
+
|
|
12
|
+
# Offense count: 3
|
|
13
|
+
Lint/Eval:
|
|
14
|
+
Enabled: false
|
|
15
|
+
|
|
16
|
+
# Offense count: 13
|
|
17
|
+
# Cop supports --auto-correct.
|
|
18
|
+
Lint/RescueException:
|
|
19
|
+
Enabled: false
|
|
20
|
+
|
|
21
|
+
# Offense count: 9
|
|
22
|
+
# Cop supports --auto-correct.
|
|
23
|
+
Lint/StringConversionInInterpolation:
|
|
24
|
+
Enabled: true
|
|
25
|
+
|
|
26
|
+
# Offense count: 9
|
|
27
|
+
# Cop supports --auto-correct.
|
|
28
|
+
Lint/UnusedBlockArgument:
|
|
29
|
+
Enabled: false
|
|
30
|
+
|
|
31
|
+
# Offense count: 18
|
|
32
|
+
# Cop supports --auto-correct.
|
|
33
|
+
Lint/UnusedMethodArgument:
|
|
34
|
+
Enabled: false
|
|
35
|
+
|
|
36
|
+
# Offense count: 5
|
|
37
|
+
Metrics/BlockNesting:
|
|
38
|
+
Max: 4
|
|
39
|
+
|
|
40
|
+
Style/SymbolProc:
|
|
41
|
+
Enabled: false
|
data/.rubocop_todo.yml
ADDED
|
@@ -0,0 +1,111 @@
|
|
|
1
|
+
# This configuration was generated by `rubocop --auto-gen-config`
|
|
2
|
+
# on 2015-09-11 14:29:44 +0300 using RuboCop version 0.32.1.
|
|
3
|
+
# The point is for the user to remove these configuration records
|
|
4
|
+
# one by one as the offenses are removed from the code base.
|
|
5
|
+
# Note that changes in the inspected code, or installation of new
|
|
6
|
+
# versions of RuboCop, may require this file to be generated again.
|
|
7
|
+
|
|
8
|
+
# Offense count: 9
|
|
9
|
+
Metrics/AbcSize:
|
|
10
|
+
Max: 29
|
|
11
|
+
|
|
12
|
+
# Offense count: 54
|
|
13
|
+
# Configuration parameters: AllowURI, URISchemes.
|
|
14
|
+
Metrics/LineLength:
|
|
15
|
+
Max: 184
|
|
16
|
+
|
|
17
|
+
# Offense count: 7
|
|
18
|
+
# Configuration parameters: CountComments.
|
|
19
|
+
Metrics/MethodLength:
|
|
20
|
+
Max: 24
|
|
21
|
+
|
|
22
|
+
# Offense count: 3
|
|
23
|
+
# Cop supports --auto-correct.
|
|
24
|
+
# Configuration parameters: IndentWhenRelativeTo, SupportedStyles, IndentOneStep.
|
|
25
|
+
Style/CaseIndentation:
|
|
26
|
+
Enabled: false
|
|
27
|
+
|
|
28
|
+
# Offense count: 9
|
|
29
|
+
# Configuration parameters: EnforcedStyle, SupportedStyles.
|
|
30
|
+
Style/ClassAndModuleChildren:
|
|
31
|
+
Enabled: false
|
|
32
|
+
|
|
33
|
+
# Offense count: 1
|
|
34
|
+
Style/ClassVars:
|
|
35
|
+
Enabled: false
|
|
36
|
+
|
|
37
|
+
# Offense count: 4
|
|
38
|
+
# Cop supports --auto-correct.
|
|
39
|
+
Style/ColonMethodCall:
|
|
40
|
+
Enabled: false
|
|
41
|
+
|
|
42
|
+
# Offense count: 13
|
|
43
|
+
Style/Documentation:
|
|
44
|
+
Enabled: false
|
|
45
|
+
|
|
46
|
+
# Offense count: 1
|
|
47
|
+
# Configuration parameters: Exclude.
|
|
48
|
+
Style/FileName:
|
|
49
|
+
Enabled: false
|
|
50
|
+
|
|
51
|
+
# Offense count: 25
|
|
52
|
+
# Cop supports --auto-correct.
|
|
53
|
+
# Configuration parameters: SupportedStyles, UseHashRocketsWithSymbolValues.
|
|
54
|
+
Style/HashSyntax:
|
|
55
|
+
EnforcedStyle: hash_rockets
|
|
56
|
+
|
|
57
|
+
# Offense count: 2
|
|
58
|
+
# Cop supports --auto-correct.
|
|
59
|
+
# Configuration parameters: Width.
|
|
60
|
+
Style/IndentationWidth:
|
|
61
|
+
Enabled: false
|
|
62
|
+
|
|
63
|
+
# Offense count: 1
|
|
64
|
+
# Cop supports --auto-correct.
|
|
65
|
+
Style/NegatedIf:
|
|
66
|
+
Enabled: false
|
|
67
|
+
|
|
68
|
+
# Offense count: 4
|
|
69
|
+
# Configuration parameters: EnforcedStyle, SupportedStyles.
|
|
70
|
+
Style/RaiseArgs:
|
|
71
|
+
Enabled: false
|
|
72
|
+
|
|
73
|
+
# Offense count: 7
|
|
74
|
+
# Cop supports --auto-correct.
|
|
75
|
+
# Configuration parameters: EnforcedStyle, SupportedStyles.
|
|
76
|
+
Style/SignalException:
|
|
77
|
+
Enabled: false
|
|
78
|
+
|
|
79
|
+
# Offense count: 1
|
|
80
|
+
# Cop supports --auto-correct.
|
|
81
|
+
Style/SpaceAfterComma:
|
|
82
|
+
Enabled: false
|
|
83
|
+
|
|
84
|
+
# Offense count: 2
|
|
85
|
+
# Cop supports --auto-correct.
|
|
86
|
+
# Configuration parameters: MultiSpaceAllowedForOperators.
|
|
87
|
+
Style/SpaceAroundOperators:
|
|
88
|
+
Enabled: false
|
|
89
|
+
|
|
90
|
+
# Offense count: 2
|
|
91
|
+
# Cop supports --auto-correct.
|
|
92
|
+
# Configuration parameters: EnforcedStyle, EnforcedStyleForEmptyBraces, SupportedStyles.
|
|
93
|
+
Style/SpaceInsideHashLiteralBraces:
|
|
94
|
+
Enabled: false
|
|
95
|
+
|
|
96
|
+
# Offense count: 43
|
|
97
|
+
# Cop supports --auto-correct.
|
|
98
|
+
# Configuration parameters: EnforcedStyle, SupportedStyles.
|
|
99
|
+
Style/StringLiterals:
|
|
100
|
+
Enabled: false
|
|
101
|
+
|
|
102
|
+
# Offense count: 2
|
|
103
|
+
# Cop supports --auto-correct.
|
|
104
|
+
# Configuration parameters: EnforcedStyle, SupportedStyles.
|
|
105
|
+
Style/TrailingBlankLines:
|
|
106
|
+
Enabled: false
|
|
107
|
+
|
|
108
|
+
# Offense count: 4
|
|
109
|
+
# Cop supports --auto-correct.
|
|
110
|
+
Style/TrailingWhitespace:
|
|
111
|
+
Enabled: false
|
data/Gemfile
ADDED
data/README.md
CHANGED
|
@@ -1,19 +1,20 @@
|
|
|
1
1
|
# OpenSCAP plug-in for Foreman Proxy
|
|
2
2
|
|
|
3
3
|
A plug-in to the Foreman Proxy which receives bzip2ed ARF files
|
|
4
|
-
and forwards them to the Foreman.
|
|
4
|
+
and forwards them as JSON to the Foreman.
|
|
5
|
+
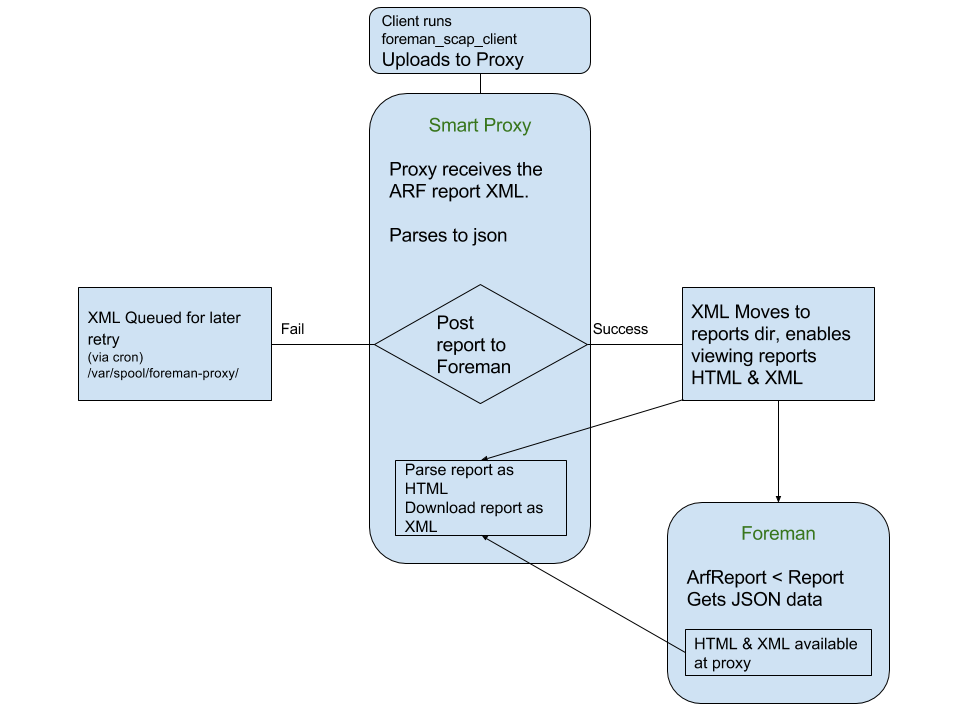
smart_proxy_openscap plugin is required for the normal operation of OpenSCAP in the Foreman.
|
|
5
6
|
|
|
6
|
-
|
|
7
|
-
the client machine. Proxy caches collected ARF files until they
|
|
8
|
-
are forwarded to Foreman.
|
|
7
|
+
## How it works
|
|
9
8
|
|
|
10
|
-
|
|
9
|
+
Incoming ARF files are authenticated using either puppet certificate or Katello certificate of
|
|
10
|
+
the client machine. The ARF files are parsed on the proxy and posted to the Foreman as JSON reports
|
|
11
|
+
and the ARF files are saved in a reports directory, where they can be accessed for full HTML report or
|
|
12
|
+
downloaded as bzip2ed xml report.
|
|
13
|
+
If posting is failed, the ARF files are saved in queue for later retry.
|
|
11
14
|
|
|
12
|
-
|
|
13
|
-
|
|
14
|
-
- Install foreman-proxy from Foreman-proxy upstream
|
|
15
|
+
Learn more about [Foreman-OpenSCAP](https://github.com/theforeman/foreman_openscap) workflow.
|
|
15
16
|
|
|
16
|
-
|
|
17
|
+
## Installation from RPMs
|
|
17
18
|
|
|
18
19
|
- Install smart_proxy_openscap
|
|
19
20
|
|
|
@@ -22,40 +23,40 @@ Learn more about [Foreman-OpenSCAP](https://github.com/OpenSCAP/foreman_openscap
|
|
|
22
23
|
```
|
|
23
24
|
|
|
24
25
|
## Installation from upstream git
|
|
25
|
-
|
|
26
|
-
|
|
27
|
-
- Download smart_proxy_openscap
|
|
28
|
-
|
|
29
|
-
```
|
|
30
|
-
~$ git clone https://github.com/OpenSCAP/smart_proxy_openscap.git
|
|
31
|
-
```
|
|
32
|
-
|
|
33
|
-
- Build smart_proxy_openscap RPM
|
|
34
|
-
|
|
35
|
-
```
|
|
36
|
-
~$ cd smart_proxy_openscap
|
|
37
|
-
~$ gem build smart_proxy_openscap.gemspec
|
|
38
|
-
~# yum install yum-utils rpm-build
|
|
39
|
-
~# yum-builddep extra/rubygem-smartproxy_openscap.spec
|
|
40
|
-
~# rpmbuild --define "_sourcedir `pwd`" -ba extra/rubygem-smart_proxy_openscap.spec
|
|
41
|
-
```
|
|
42
|
-
|
|
43
|
-
- Install rubygem-smart_proxy_openscap
|
|
44
|
-
|
|
26
|
+
- Add smart_proxy_openscap to your smart proxy `bundler.d/openscap.rb` gemfile:
|
|
27
|
+
|
|
45
28
|
```
|
|
46
|
-
~$
|
|
29
|
+
~$ gem 'smart_proxy_openscap', :git => https://github.com/theforeman/smart_proxy_openscap.git
|
|
47
30
|
```
|
|
48
31
|
|
|
49
|
-
If you don't install through RPM
|
|
50
|
-
/var/spool/foreman-proxy
|
|
51
|
-
foreman-proxy runs.
|
|
32
|
+
If you don't install through RPM and you are using bundler, you may need to create
|
|
33
|
+
/var/spool/foreman-proxy & /usr/share/foreman-proxy/openscap directories manually and
|
|
34
|
+
set it's owner to the user under which foreman-proxy runs.
|
|
52
35
|
|
|
53
36
|
## Configuration
|
|
54
37
|
|
|
55
38
|
```
|
|
56
39
|
cp /etc/foreman-proxy/settings.d/openscap.yml{.example,}
|
|
57
|
-
|
|
58
|
-
|
|
40
|
+
```
|
|
41
|
+
Configure the following parameters so it would look like:
|
|
42
|
+
|
|
43
|
+
```
|
|
44
|
+
---
|
|
45
|
+
:enabled: true
|
|
46
|
+
|
|
47
|
+
# Log file for the forwarding script.
|
|
48
|
+
:openscap_send_log_file: /var/log/foreman-proxy/openscap-send.log
|
|
49
|
+
|
|
50
|
+
# Directory where OpenSCAP audits are stored
|
|
51
|
+
# before they are forwarded to Foreman
|
|
52
|
+
:spooldir: /var/spool/foreman-proxy/openscap
|
|
53
|
+
|
|
54
|
+
# Directory where OpenSCAP content XML are stored
|
|
55
|
+
# So we will not request the XML from Foreman each time
|
|
56
|
+
:contentdir: /var/lib/openscap/content
|
|
57
|
+
# Directory where OpenSCAP report XML are stored
|
|
58
|
+
# So Foreman can request arf xml reports
|
|
59
|
+
:reportsdir: /usr/share/foreman-proxy/openscap/content
|
|
59
60
|
```
|
|
60
61
|
|
|
61
62
|
- Deploy
|
|
@@ -64,9 +65,29 @@ foreman-proxy runs.
|
|
|
64
65
|
~# service foreman-proxy restart
|
|
65
66
|
```
|
|
66
67
|
|
|
67
|
-
|
|
68
|
+
## Usage
|
|
69
|
+
|
|
70
|
+
|
|
71
|
+
|
|
72
|
+
### Exposed APIs
|
|
73
|
+
|
|
74
|
+
* POST "/compliance/arf/:policy" - API to recieve ARF files, parse them and post to the Foreman. `:policy` is the policy ID from Foreman. expects ARF bzip2 file as POST body
|
|
75
|
+
|
|
76
|
+
* GET "/compliance/arf/:id/:cname/:date/:digest/xml" - API to download bizped2 ARF file. `:id` - ArfReport id, `:cname` - Host name, `:date` - Report date, `:digest` - Digest of the Arf file
|
|
77
|
+
|
|
78
|
+
* GET "/compliance/arf/:id/:cname/:date/:digest/html" - API to fetch full HTML report. `:id` - ArfReport id, `:cname` - Host name, `:date` - Report date, `:digest` - Digest of the Arf file
|
|
79
|
+
|
|
80
|
+
* GET "/compliance/policies/:policy_id/content" - API to download and serve SCAP content file for policy. `:policy_id` - Policy id from Foreman
|
|
81
|
+
|
|
82
|
+
* POST "/compliance/scap_content/policies" - API to extract policies from SCAP content. expects SCAP content posted as the POST body
|
|
83
|
+
|
|
84
|
+
* POST "/compliance/scap_content/validator" - API to validate SCAP content. expects SCAP content posted as the POST body
|
|
85
|
+
|
|
86
|
+
* POST "/compliance/scap_content/guide/:policy" - API to return Policy's HTML guide. `:policy` - policy name. expects SCAP content posted as the POST body
|
|
87
|
+
|
|
88
|
+
### Binaries
|
|
68
89
|
|
|
69
|
-
|
|
90
|
+
* `smart_proxy_openscap_send` - Sends failed ARF files to Foreman (in case first try failed). When installed with RPM, a cron jobs is configured to run every 30 minutes.
|
|
70
91
|
|
|
71
92
|
## Copyright
|
|
72
93
|
|
data/Rakefile
ADDED
|
@@ -0,0 +1,14 @@
|
|
|
1
|
+
require 'rake'
|
|
2
|
+
require 'rake/testtask'
|
|
3
|
+
|
|
4
|
+
desc 'Default: run unit tests.'
|
|
5
|
+
task :default => :test
|
|
6
|
+
|
|
7
|
+
desc 'Test the Smart Proxy OpenSCAP.'
|
|
8
|
+
Rake::TestTask.new(:test) do |t|
|
|
9
|
+
t.libs << '.'
|
|
10
|
+
t.libs << 'lib'
|
|
11
|
+
t.libs << 'test'
|
|
12
|
+
t.test_files = FileList['test/**/*_test.rb']
|
|
13
|
+
t.verbose = true
|
|
14
|
+
end
|
|
@@ -23,7 +23,7 @@ exit unless Proxy::OpenSCAP::Plugin.settings.enabled == true
|
|
|
23
23
|
|
|
24
24
|
module Proxy
|
|
25
25
|
module Log
|
|
26
|
-
@@logger = ::Logger.new(Proxy::OpenSCAP::Plugin.settings.openscap_send_log_file, 6, 1024*1024*10)
|
|
26
|
+
@@logger = ::Logger.new(Proxy::OpenSCAP.fullpath(Proxy::OpenSCAP::Plugin.settings.openscap_send_log_file), 6, 1024*1024*10)
|
|
27
27
|
@@logger.level = ::Logger.const_get(Proxy::SETTINGS.log_level.upcase)
|
|
28
28
|
end
|
|
29
29
|
end
|
|
@@ -0,0 +1,58 @@
|
|
|
1
|
+
module Proxy::OpenSCAP
|
|
2
|
+
class FetchScapContent
|
|
3
|
+
include ::Proxy::Log
|
|
4
|
+
def get_policy_content(policy_id)
|
|
5
|
+
policy_store_dir = File.join(Proxy::OpenSCAP.fullpath(Proxy::OpenSCAP::Plugin.settings.contentdir), policy_id.to_s)
|
|
6
|
+
policy_scap_file = File.join(policy_store_dir, "#{policy_id}_scap_content.xml")
|
|
7
|
+
begin
|
|
8
|
+
logger.info "Creating directory to store SCAP file: #{policy_store_dir}"
|
|
9
|
+
FileUtils.mkdir_p(policy_store_dir) # will fail silently if exists
|
|
10
|
+
rescue Errno::EACCES => e
|
|
11
|
+
logger.error "No permission to create directory #{policy_store_dir}"
|
|
12
|
+
raise e
|
|
13
|
+
rescue StandardError => e
|
|
14
|
+
logger.error "Could not create '#{policy_store_dir}' directory: #{e.message}"
|
|
15
|
+
raise e
|
|
16
|
+
end
|
|
17
|
+
|
|
18
|
+
scap_file = policy_content_file(policy_scap_file)
|
|
19
|
+
scap_file ||= save_or_serve_scap_file(policy_id, policy_scap_file)
|
|
20
|
+
scap_file
|
|
21
|
+
end
|
|
22
|
+
|
|
23
|
+
private
|
|
24
|
+
|
|
25
|
+
def policy_content_file(policy_scap_file)
|
|
26
|
+
return nil if !File.file?(policy_scap_file) || File.zero?(policy_scap_file)
|
|
27
|
+
File.open(policy_scap_file, 'rb').read
|
|
28
|
+
end
|
|
29
|
+
|
|
30
|
+
def save_or_serve_scap_file(policy_id, policy_scap_file)
|
|
31
|
+
lock = Proxy::FileLock::try_locking(policy_scap_file)
|
|
32
|
+
response = fetch_scap_content_xml(policy_id, policy_scap_file)
|
|
33
|
+
if lock.nil?
|
|
34
|
+
return response
|
|
35
|
+
else
|
|
36
|
+
begin
|
|
37
|
+
File.open(policy_scap_file, 'wb') do |file|
|
|
38
|
+
file << response
|
|
39
|
+
end
|
|
40
|
+
ensure
|
|
41
|
+
Proxy::FileLock::unlock(lock)
|
|
42
|
+
end
|
|
43
|
+
scap_file = policy_content_file(policy_scap_file)
|
|
44
|
+
raise FileNotFound if scap_file.nil?
|
|
45
|
+
return scap_file
|
|
46
|
+
end
|
|
47
|
+
end
|
|
48
|
+
|
|
49
|
+
def fetch_scap_content_xml(policy_id, policy_scap_file)
|
|
50
|
+
foreman_request = Proxy::HttpRequest::ForemanRequest.new
|
|
51
|
+
policy_content_path = "api/v2/compliance/policies/#{policy_id}/content"
|
|
52
|
+
req = foreman_request.request_factory.create_get(policy_content_path)
|
|
53
|
+
response = foreman_request.send_request(req)
|
|
54
|
+
response.value
|
|
55
|
+
response.body
|
|
56
|
+
end
|
|
57
|
+
end
|
|
58
|
+
end
|
|
@@ -0,0 +1,38 @@
|
|
|
1
|
+
module Proxy::OpenSCAP
|
|
2
|
+
class ForemanForwarder < Proxy::HttpRequest::ForemanRequest
|
|
3
|
+
include ::Proxy::Log
|
|
4
|
+
|
|
5
|
+
def post_arf_report(cname, policy_id, date, data)
|
|
6
|
+
begin
|
|
7
|
+
json_data = Proxy::OpenSCAP::Parse.new(data).as_json
|
|
8
|
+
foreman_api_path = upload_path(cname, policy_id, date)
|
|
9
|
+
response = send_request(foreman_api_path, json_data)
|
|
10
|
+
# Raise an HTTP error if the response is not 2xx (success).
|
|
11
|
+
response.value
|
|
12
|
+
res = JSON.parse(response.body)
|
|
13
|
+
raise StandardError, "Received response: #{response.code} #{response.msg}" unless res['result'] == 'OK'
|
|
14
|
+
rescue StandardError => e
|
|
15
|
+
logger.debug response.body if response
|
|
16
|
+
logger.debug e.backtrace.join("\n\t")
|
|
17
|
+
raise e
|
|
18
|
+
end
|
|
19
|
+
res
|
|
20
|
+
end
|
|
21
|
+
|
|
22
|
+
private
|
|
23
|
+
|
|
24
|
+
def upload_path(cname, policy_id, date)
|
|
25
|
+
"/api/v2/compliance/arf_reports/#{cname}/#{policy_id}/#{date}"
|
|
26
|
+
end
|
|
27
|
+
|
|
28
|
+
def send_request(path, body)
|
|
29
|
+
# Override the parent method to set the right headers
|
|
30
|
+
path = [uri.path, path].join('/') unless uri.path.empty?
|
|
31
|
+
req = Net::HTTP::Post.new(URI.join(uri.to_s, path).path)
|
|
32
|
+
req.add_field('Accept', 'application/json,version=2')
|
|
33
|
+
req.content_type = 'application/json'
|
|
34
|
+
req.body = body
|
|
35
|
+
http.request(req)
|
|
36
|
+
end
|
|
37
|
+
end
|
|
38
|
+
end
|
|
@@ -7,49 +7,108 @@
|
|
|
7
7
|
# FOR A PARTICULAR PURPOSE. You should have received a copy of GPLv3
|
|
8
8
|
# along with this software; if not, see http://www.gnu.org/licenses/gpl.txt
|
|
9
9
|
#
|
|
10
|
-
|
|
11
10
|
require 'smart_proxy_openscap/openscap_lib'
|
|
12
11
|
|
|
13
12
|
module Proxy::OpenSCAP
|
|
13
|
+
HTTP_ERRORS = [
|
|
14
|
+
EOFError,
|
|
15
|
+
Errno::ECONNRESET,
|
|
16
|
+
Errno::EINVAL,
|
|
17
|
+
Net::HTTPBadResponse,
|
|
18
|
+
Net::HTTPHeaderSyntaxError,
|
|
19
|
+
Net::ProtocolError,
|
|
20
|
+
Timeout::Error
|
|
21
|
+
]
|
|
22
|
+
|
|
14
23
|
class Api < ::Sinatra::Base
|
|
15
24
|
include ::Proxy::Log
|
|
16
25
|
helpers ::Proxy::Helpers
|
|
17
26
|
authorize_with_ssl_client
|
|
18
27
|
|
|
19
|
-
|
|
28
|
+
post "/arf/:policy" do
|
|
20
29
|
# first let's verify client's certificate
|
|
21
30
|
begin
|
|
22
31
|
cn = Proxy::OpenSCAP::common_name request
|
|
23
32
|
rescue Proxy::Error::Unauthorized => e
|
|
24
33
|
log_halt 403, "Client authentication failed: #{e.message}"
|
|
25
34
|
end
|
|
35
|
+
date = Time.now.to_i
|
|
36
|
+
policy = params[:policy]
|
|
26
37
|
|
|
27
|
-
# validate the url (i.e. avoid malformed :policy)
|
|
28
38
|
begin
|
|
29
|
-
|
|
30
|
-
|
|
31
|
-
|
|
32
|
-
rescue
|
|
33
|
-
|
|
39
|
+
post_to_foreman = ForemanForwarder.new.post_arf_report(cn, policy, date, request.body.string)
|
|
40
|
+
Proxy::OpenSCAP::StorageFS.new(Proxy::OpenSCAP::Plugin.settings.reportsdir, cn, post_to_foreman['id'], date)
|
|
41
|
+
.store_archive(request.body.string)
|
|
42
|
+
rescue Proxy::OpenSCAP::StoreReportError => e
|
|
43
|
+
Proxy::OpenSCAP::StorageFS.new(Proxy::OpenSCAP::Plugin.settings.failed_dir, cn, post_to_foreman['id'], date)
|
|
44
|
+
.store_failed(request.body.string)
|
|
45
|
+
logger.error "Failed to save Report in reports directory (#{Proxy::OpenSCAP::Plugin.settings.reportsdir}). Failed with: #{e.message}.
|
|
46
|
+
Saving file in #{Proxy::OpenSCAP::Plugin.settings.failed_dir}. Please copy manually to #{Proxy::OpenSCAP::Plugin.settings.reportsdir}"
|
|
47
|
+
rescue *HTTP_ERRORS => e
|
|
48
|
+
### If the upload to foreman fails then store it in the spooldir
|
|
49
|
+
logger.error "Failed to upload to Foreman, saving in spool. Failed with: #{e.message}"
|
|
50
|
+
Proxy::OpenSCAP::StorageFS.new(Proxy::OpenSCAP::Plugin.settings.spooldir, cn, policy, date)
|
|
51
|
+
.store_spool(request.body.string)
|
|
52
|
+
rescue Proxy::OpenSCAP::StoreSpoolError => e
|
|
53
|
+
log_halt 500, e.message
|
|
34
54
|
end
|
|
55
|
+
end
|
|
35
56
|
|
|
57
|
+
get "/arf/:id/:cname/:date/:digest/xml" do
|
|
58
|
+
content_type 'application/x-bzip2'
|
|
36
59
|
begin
|
|
37
|
-
|
|
38
|
-
|
|
39
|
-
|
|
60
|
+
Proxy::OpenSCAP::StorageFS.new(Proxy::OpenSCAP::Plugin.settings.reportsdir, params[:cname], params[:id], params[:date])
|
|
61
|
+
.get_arf_xml(params[:digest])
|
|
62
|
+
rescue FileNotFound => e
|
|
63
|
+
log_halt 500, "Could not find requested file, #{e.message}"
|
|
40
64
|
end
|
|
65
|
+
end
|
|
41
66
|
|
|
42
|
-
|
|
43
|
-
|
|
44
|
-
|
|
67
|
+
get "/arf/:id/:cname/:date/:digest/html" do
|
|
68
|
+
begin
|
|
69
|
+
Proxy::OpenSCAP::StorageFS.new(Proxy::OpenSCAP::Plugin.settings.reportsdir, params[:cname], params[:id], params[:date])
|
|
70
|
+
.get_arf_html(params[:digest])
|
|
71
|
+
rescue FileNotFound => e
|
|
72
|
+
log_halt 500, "Could not find requested file, #{e.message}"
|
|
73
|
+
end
|
|
45
74
|
end
|
|
46
75
|
|
|
47
76
|
get "/policies/:policy_id/content" do
|
|
48
77
|
content_type 'application/xml'
|
|
49
78
|
begin
|
|
50
|
-
Proxy::OpenSCAP::get_policy_content(params[:policy_id])
|
|
51
|
-
rescue
|
|
52
|
-
log_halt e.
|
|
79
|
+
Proxy::OpenSCAP::FetchScapContent.new.get_policy_content(params[:policy_id])
|
|
80
|
+
rescue *HTTP_ERRORS => e
|
|
81
|
+
log_halt e.response.code.to_i, "File not found on Foreman. Wrong policy id?"
|
|
82
|
+
rescue StandardError => e
|
|
83
|
+
log_halt 500, "Error occurred: #{e.message}"
|
|
84
|
+
end
|
|
85
|
+
end
|
|
86
|
+
|
|
87
|
+
post "/scap_content/policies" do
|
|
88
|
+
begin
|
|
89
|
+
Proxy::OpenSCAP::ContentParser.new(request.body.string).extract_policies
|
|
90
|
+
rescue *HTTP_ERRORS => e
|
|
91
|
+
log_halt 500, e.message
|
|
92
|
+
rescue StandardError => e
|
|
93
|
+
log_halt 500, "Error occurred: #{e.message}"
|
|
94
|
+
end
|
|
95
|
+
end
|
|
96
|
+
|
|
97
|
+
post "/scap_content/validator" do
|
|
98
|
+
begin
|
|
99
|
+
Proxy::OpenSCAP::ContentParser.new(request.body.string).validate
|
|
100
|
+
rescue *HTTP_ERRORS => e
|
|
101
|
+
log_halt 500, e.message
|
|
102
|
+
rescue StandardError => e
|
|
103
|
+
log_halt 500, "Error occurred: #{e.message}"
|
|
104
|
+
end
|
|
105
|
+
end
|
|
106
|
+
|
|
107
|
+
post "/scap_content/guide/:policy" do
|
|
108
|
+
begin
|
|
109
|
+
Proxy::OpenSCAP::ContentParser.new(request.body.string).guide(params[:policy])
|
|
110
|
+
rescue *HTTP_ERRORS => e
|
|
111
|
+
log_halt 500, e.message
|
|
53
112
|
rescue StandardError => e
|
|
54
113
|
log_halt 500, "Error occurred: #{e.message}"
|
|
55
114
|
end
|