pws 0.9.0 → 0.9.1
Sign up to get free protection for your applications and to get access to all the features.
- data/README.md +29 -0
- data/Rakefile +1 -0
- data/features/access.feature +13 -0
- data/features/add.feature +45 -0
- data/features/generate.feature +65 -0
- data/features/get.feature +52 -0
- data/features/master.feature +61 -0
- data/features/misc.feature +22 -0
- data/features/namespaces.feature +22 -0
- data/features/remove.feature +27 -0
- data/features/rename.feature +43 -0
- data/features/show.feature +37 -0
- data/features/step_definitions/pws_steps.rb +36 -0
- data/features/support/env.rb +41 -0
- data/lib/pws.rb +9 -1
- data/lib/pws/version.rb +1 -1
- data/pws.gemspec +3 -3
- metadata +29 -17
- data/README +0 -13
data/README.md
ADDED
|
@@ -0,0 +1,29 @@
|
|
|
1
|
+
pws 
|
|
2
|
+
===
|
|
3
|
+
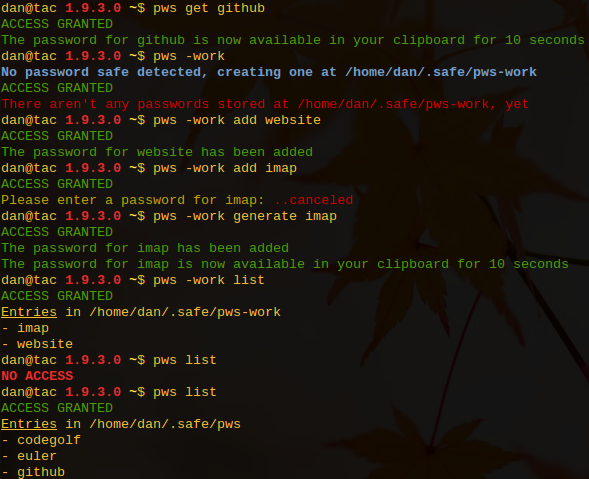
pws is a command-line password safe/manager written in Ruby.
|
|
4
|
+
|
|
5
|
+
|
|
6
|
+
|
|
7
|
+
Installation
|
|
8
|
+
---
|
|
9
|
+
You can install pws with
|
|
10
|
+
`$ gem install pws`
|
|
11
|
+
|
|
12
|
+
Run `$ pws help` for usage information.
|
|
13
|
+
|
|
14
|
+
Misc
|
|
15
|
+
---
|
|
16
|
+
Trust the code by reading the source!
|
|
17
|
+
|
|
18
|
+
Originally based on [this tutorial](http://rbjl.net/41-tutorial-build-your-own-password-safe-with-ruby)
|
|
19
|
+
|
|
20
|
+
Cucumber specs loosely based on [the ones](https://github.com/thecatwasnot/passwordsafe/blob/master/features/) by thecatwasnot - thanks
|
|
21
|
+
|
|
22
|
+
Contributions by
|
|
23
|
+
---
|
|
24
|
+
* [brianewing](https://github.com/brianewing/)
|
|
25
|
+
|
|
26
|
+
Copyright
|
|
27
|
+
---
|
|
28
|
+
|
|
29
|
+
© 2010-2012 Jan Lelis, MIT license
|
data/Rakefile
CHANGED
|
@@ -0,0 +1,13 @@
|
|
|
1
|
+
Feature: Access
|
|
2
|
+
In order to use the password safe
|
|
3
|
+
As a user
|
|
4
|
+
I want to create a new safe
|
|
5
|
+
|
|
6
|
+
Scenario: Trying to call a pws task (except help or version), but safe does not exist, yet
|
|
7
|
+
When I run `pws` interactively
|
|
8
|
+
And I type "some_new_master_password"
|
|
9
|
+
Then the output should contain "No password safe detected, creating one at"
|
|
10
|
+
And the output should contain "Please enter a new master password:"
|
|
11
|
+
And the output should contain "There aren't any passwords stored"
|
|
12
|
+
|
|
13
|
+
|
|
@@ -0,0 +1,45 @@
|
|
|
1
|
+
Feature: Add
|
|
2
|
+
In order to have passwords in my password safe
|
|
3
|
+
As a user
|
|
4
|
+
I want to add new passwords to my password safe
|
|
5
|
+
|
|
6
|
+
Scenario: Add a new password for "github"
|
|
7
|
+
Given A safe exists with master password "my_master_password"
|
|
8
|
+
When I run `pws add github` interactively
|
|
9
|
+
And I type "my_master_password"
|
|
10
|
+
And I type "github_password"
|
|
11
|
+
Then the output should contain "Master password:"
|
|
12
|
+
And the output should contain "Please enter a password for github:"
|
|
13
|
+
And the output should contain "The password for github has been added"
|
|
14
|
+
|
|
15
|
+
Scenario: Add a new password for "github", already passing it as command line paramenter (not recommended)
|
|
16
|
+
Given A safe exists with master password "my_master_password"
|
|
17
|
+
When I run `pws add github github_password` interactively
|
|
18
|
+
And I type "my_master_password"
|
|
19
|
+
Then the output should contain "Master password:"
|
|
20
|
+
And the output should contain "The password for github has been added"
|
|
21
|
+
|
|
22
|
+
Scenario: Try to add a new password for "github" (but it already exists)
|
|
23
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
24
|
+
When I run `pws add github` interactively
|
|
25
|
+
And I type "my_master_password"
|
|
26
|
+
Then the output should contain "Master password:"
|
|
27
|
+
And the output should contain "There is already a password stored for github. You need to remove it before creating a new one!"
|
|
28
|
+
|
|
29
|
+
Scenario: Try to add a new password for "github" (but it's empty)
|
|
30
|
+
Given A safe exists with master password "my_master_password"
|
|
31
|
+
When I run `pws add github` interactively
|
|
32
|
+
And I type "my_master_password"
|
|
33
|
+
And I type ""
|
|
34
|
+
Then the output should contain "Master password:"
|
|
35
|
+
And the output should contain "Please enter a password for github:"
|
|
36
|
+
And the output should contain "Cannot add an empty password!"
|
|
37
|
+
|
|
38
|
+
Scenario: Try to add a new password for "github" (but the master password is wrong)
|
|
39
|
+
Given A safe exists with master password "my_master_password"
|
|
40
|
+
When I run `pws add github` interactively
|
|
41
|
+
And I type "my_master_password_wrong"
|
|
42
|
+
Then the output should contain "Master password:"
|
|
43
|
+
And the output should contain "NO ACCESS"
|
|
44
|
+
|
|
45
|
+
|
|
@@ -0,0 +1,65 @@
|
|
|
1
|
+
Feature: Generate
|
|
2
|
+
In order to have safe passwords in my password safe
|
|
3
|
+
As a user
|
|
4
|
+
I want to generate passwords and add them to my password safe
|
|
5
|
+
|
|
6
|
+
@wait-11s
|
|
7
|
+
@slow-hack
|
|
8
|
+
Scenario: Generate a new password for "github" and gets it
|
|
9
|
+
Given A safe exists with master password "my_master_password"
|
|
10
|
+
When I run `pws generate github` interactively
|
|
11
|
+
And I type "my_master_password"
|
|
12
|
+
Then the output should contain "Master password:"
|
|
13
|
+
And the output should contain "The password for github has been added"
|
|
14
|
+
And the output should contain "The password for github is now available in your clipboard for 10 seconds"
|
|
15
|
+
|
|
16
|
+
@slow-hack
|
|
17
|
+
Scenario: Generate a new password for "github", second parameter gets passed to the get as keep-in-clipboard time
|
|
18
|
+
Given A safe exists with master password "my_master_password"
|
|
19
|
+
When I run `pws generate github 1` interactively
|
|
20
|
+
And I type "my_master_password"
|
|
21
|
+
Then the output should contain "Master password:"
|
|
22
|
+
And the output should contain "The password for github has been added"
|
|
23
|
+
And the output should contain "The password for github is now available in your clipboard for 1 second"
|
|
24
|
+
|
|
25
|
+
@slow-hack
|
|
26
|
+
Scenario: Generate a new password for "github", third parameter defines password length
|
|
27
|
+
Given A safe exists with master password "my_master_password"
|
|
28
|
+
When I run `pws generate github 0 10` interactively
|
|
29
|
+
And I type "my_master_password"
|
|
30
|
+
Then the output should contain "Master password:"
|
|
31
|
+
And the output should contain "The password for github has been added"
|
|
32
|
+
And the output should contain "The password for github has been copied to your clipboard"
|
|
33
|
+
And the clipboard should match /^.{10}$/
|
|
34
|
+
|
|
35
|
+
@slow-hack
|
|
36
|
+
Scenario: Generate a new password for "github", default length is 64
|
|
37
|
+
Given A safe exists with master password "my_master_password"
|
|
38
|
+
When I run `pws generate github 0` interactively
|
|
39
|
+
And I type "my_master_password"
|
|
40
|
+
Then the output should contain "Master password:"
|
|
41
|
+
And the output should contain "The password for github has been added"
|
|
42
|
+
And the output should contain "The password for github has been copied to your clipboard"
|
|
43
|
+
And the clipboard should match /^.{64}$/
|
|
44
|
+
|
|
45
|
+
@slow-hack
|
|
46
|
+
Scenario: Generate a new password for "github", fourth parameter defines a char pool used for generation
|
|
47
|
+
Given A safe exists with master password "my_master_password"
|
|
48
|
+
When I run `pws generate github 0 10 a` interactively
|
|
49
|
+
And I type "my_master_password"
|
|
50
|
+
Then the output should contain "Master password:"
|
|
51
|
+
And the output should contain "The password for github has been added"
|
|
52
|
+
And the output should contain "The password for github has been copied to your clipboard"
|
|
53
|
+
And the clipboard should match /^a{10}$/
|
|
54
|
+
|
|
55
|
+
@slow-hack
|
|
56
|
+
Scenario: Generate a new password for "github", the default char pool is !\"\#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\\]^_`abcdefghijklmnopqrstuvwxyz{|}~
|
|
57
|
+
Given A safe exists with master password "my_master_password"
|
|
58
|
+
When I run `pws generate github 0` interactively
|
|
59
|
+
And I type "my_master_password"
|
|
60
|
+
Then the output should contain "Master password:"
|
|
61
|
+
And the output should contain "The password for github has been added"
|
|
62
|
+
And the output should contain "The password for github has been copied to your clipboard"
|
|
63
|
+
And the clipboard should match ^[!\"\#$%&'()*+,\-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ\[\\\]^_`abcdefghijklmnopqrstuvwxyz{|}~]+$
|
|
64
|
+
|
|
65
|
+
|
|
@@ -0,0 +1,52 @@
|
|
|
1
|
+
Feature: Get
|
|
2
|
+
In order to have a helpful password safe
|
|
3
|
+
As a user
|
|
4
|
+
I want to get passwords from my password safe
|
|
5
|
+
|
|
6
|
+
Scenario: Get the password for "github" (which exists) and copy it to the clipboard
|
|
7
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
8
|
+
When I run `pws get github 0` interactively
|
|
9
|
+
And I type "my_master_password"
|
|
10
|
+
Then the output should contain "Master password:"
|
|
11
|
+
And the output should contain "The password for github has been copied to your clipboard"
|
|
12
|
+
And the clipboard should contain "github_password"
|
|
13
|
+
|
|
14
|
+
@wait-11s
|
|
15
|
+
Scenario: Get the password for "github" (which exists) and keep it in the clipboard for 10 seconds
|
|
16
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
17
|
+
When I run `pws get github` interactively
|
|
18
|
+
And I type "my_master_password"
|
|
19
|
+
Then the output should contain "Master password:"
|
|
20
|
+
And the output should contain "The password for github is now available in your clipboard for 10 seconds"
|
|
21
|
+
|
|
22
|
+
Scenario: Get the password for "github" (which exists) and keep it in the clipboard for 1 second
|
|
23
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
24
|
+
When I run `pws get github 1` interactively
|
|
25
|
+
And I type "my_master_password"
|
|
26
|
+
Then the output should contain "Master password:"
|
|
27
|
+
And the output should contain "The password for github is now available in your clipboard for 1 second"
|
|
28
|
+
|
|
29
|
+
Scenario: Get the password for "github" (which exists) and ensure that the original clipboard content gets restored
|
|
30
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
31
|
+
Given A clipboard content of "blubb"
|
|
32
|
+
When I run `pws get github 1` interactively
|
|
33
|
+
And I type "my_master_password"
|
|
34
|
+
Then the output should contain "Master password:"
|
|
35
|
+
And the output should contain "The password for github is now available in your clipboard for 1 second"
|
|
36
|
+
And the clipboard should contain "blubb"
|
|
37
|
+
|
|
38
|
+
Scenario: Try to get the password for "google" (which does not exist)
|
|
39
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
40
|
+
When I run `pws get google` interactively
|
|
41
|
+
And I type "my_master_password"
|
|
42
|
+
Then the output should contain "Master password:"
|
|
43
|
+
And the output should contain "No password found for google!"
|
|
44
|
+
|
|
45
|
+
Scenario: Try to get the password for "github" (but the master password is wrong)
|
|
46
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
47
|
+
When I run `pws get github` interactively
|
|
48
|
+
And I type "my_master_password_wrong"
|
|
49
|
+
Then the output should contain "Master password:"
|
|
50
|
+
And the output should contain "NO ACCESS"
|
|
51
|
+
|
|
52
|
+
|
|
@@ -0,0 +1,61 @@
|
|
|
1
|
+
Feature: Master
|
|
2
|
+
In order to keep my passwords safe
|
|
3
|
+
As a user
|
|
4
|
+
I want to change the master password
|
|
5
|
+
|
|
6
|
+
@slow-hack
|
|
7
|
+
Scenario: Change the master password and check that it has changed
|
|
8
|
+
Given A safe exists with master password "my_master_password"
|
|
9
|
+
When I run `pws master` interactively
|
|
10
|
+
And I type "my_master_password"
|
|
11
|
+
And I type "my_new_master_password"
|
|
12
|
+
And I type "my_new_master_password"
|
|
13
|
+
Then the output should contain "Master password"
|
|
14
|
+
And the output should contain "Please enter the new master password"
|
|
15
|
+
And the output should contain "again"
|
|
16
|
+
And the output should contain "The master password has been changed"
|
|
17
|
+
When I run `pws` interactively
|
|
18
|
+
And I type "my_master_password"
|
|
19
|
+
And the output from "pws" should contain "Master password"
|
|
20
|
+
And the output from "pws" should contain "NO ACCESS"
|
|
21
|
+
|
|
22
|
+
Scenario: Try to change the master password (but password confirmation is wrong)
|
|
23
|
+
Given A safe exists with master password "my_master_password"
|
|
24
|
+
When I run `pws master` interactively
|
|
25
|
+
And I type "my_master_password"
|
|
26
|
+
And I type "my_new_master_password"
|
|
27
|
+
And I type "my_new_master_password_wrong"
|
|
28
|
+
Then the output should contain "Master password"
|
|
29
|
+
And the output should contain "Please enter the new master password"
|
|
30
|
+
And the output should contain "again"
|
|
31
|
+
And the output should contain "don't match"
|
|
32
|
+
|
|
33
|
+
Scenario: Change the master password, already passing it as command line parameter (not recommended)
|
|
34
|
+
Given A safe exists with master password "my_master_password"
|
|
35
|
+
When I run `pws master my_new_master_password` interactively
|
|
36
|
+
And I type "my_master_password"
|
|
37
|
+
Then the output should contain "Master password:"
|
|
38
|
+
And the output should contain "The master password has been changed"
|
|
39
|
+
|
|
40
|
+
@slow-hack
|
|
41
|
+
Scenario: I can have an empty master password (not recommended)
|
|
42
|
+
Given A safe exists with master password "my_master_password"
|
|
43
|
+
When I run `pws master` interactively
|
|
44
|
+
And I type "my_master_password"
|
|
45
|
+
And I type ""
|
|
46
|
+
And I type ""
|
|
47
|
+
Then the output should contain "Master password:"
|
|
48
|
+
And the output should contain "The master password has been changed"
|
|
49
|
+
When I run `pws` interactively
|
|
50
|
+
And I type ""
|
|
51
|
+
Then the output from "pws" should contain "Master password:"
|
|
52
|
+
And the output from "pws" should contain "There aren't any passwords stored"
|
|
53
|
+
|
|
54
|
+
Scenario: Try to change the master password (but enter the old one wrong)
|
|
55
|
+
Given A safe exists with master password "my_master_password"
|
|
56
|
+
When I run `pws master` interactively
|
|
57
|
+
And I type "my_master_password_wrong"
|
|
58
|
+
Then the output should contain "Master password:"
|
|
59
|
+
And the output should contain "NO ACCESS"
|
|
60
|
+
|
|
61
|
+
|
|
@@ -0,0 +1,22 @@
|
|
|
1
|
+
Feature: Misc
|
|
2
|
+
In order to be happy with my passwords safe
|
|
3
|
+
As a user
|
|
4
|
+
I want ensure the password safe behaves nicely
|
|
5
|
+
|
|
6
|
+
@slow-hack
|
|
7
|
+
Scenario: I am calling with a wrong argument count
|
|
8
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
9
|
+
When I run `pws get` interactively
|
|
10
|
+
And I type "my_master_password"
|
|
11
|
+
And the output should contain "Wrong number of arguments"
|
|
12
|
+
When I run `pws get github with far too many args` interactively
|
|
13
|
+
And I type "my_master_password"
|
|
14
|
+
And the output from "pws get github with far too many args" should contain "Wrong number of arguments"
|
|
15
|
+
|
|
16
|
+
Scenario: I am calling a task that does not exist
|
|
17
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
18
|
+
When I run `pws blubb` interactively
|
|
19
|
+
And the output should contain "Unknown action"
|
|
20
|
+
And the output should contain "blubb"
|
|
21
|
+
|
|
22
|
+
|
|
@@ -0,0 +1,22 @@
|
|
|
1
|
+
Feature: Namespaces
|
|
2
|
+
In order to keep things separate
|
|
3
|
+
As a user
|
|
4
|
+
I want to use different safes
|
|
5
|
+
|
|
6
|
+
Scenario: Use a pws namespace
|
|
7
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
8
|
+
When I run `pws -work show` interactively
|
|
9
|
+
And I type "some_new_master_password"
|
|
10
|
+
Then the output should match /No password safe detected, creating one at.*pws.*-work/
|
|
11
|
+
And the output should contain "Please enter a new master password:"
|
|
12
|
+
And the output should contain "There aren't any passwords stored"
|
|
13
|
+
|
|
14
|
+
Scenario: Only passing "-" operates on usual main namespace
|
|
15
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
16
|
+
When I run `pws - show` interactively
|
|
17
|
+
And I type "my_master_password"
|
|
18
|
+
Then the output should contain "Master password:"
|
|
19
|
+
And the output should contain "Entries"
|
|
20
|
+
And the output should contain "github"
|
|
21
|
+
|
|
22
|
+
|
|
@@ -0,0 +1,27 @@
|
|
|
1
|
+
Feature: Remove
|
|
2
|
+
In order to keep my password safe clean
|
|
3
|
+
As a user
|
|
4
|
+
I want to remove passwords from my password safe
|
|
5
|
+
|
|
6
|
+
Scenario: Remove password entry "github"
|
|
7
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
8
|
+
When I run `pws remove github` interactively
|
|
9
|
+
And I type "my_master_password"
|
|
10
|
+
Then the output should contain "Master password:"
|
|
11
|
+
And the output should contain "The password for github has been removed"
|
|
12
|
+
|
|
13
|
+
Scenario: Try to remove password entry for "google" (which does not exist)
|
|
14
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
15
|
+
When I run `pws remove google` interactively
|
|
16
|
+
And I type "my_master_password"
|
|
17
|
+
Then the output should contain "Master password:"
|
|
18
|
+
And the output should contain "No password found for google!"
|
|
19
|
+
|
|
20
|
+
Scenario: Try to remove password entry "github" (but the master password is wrong)
|
|
21
|
+
Given A safe exists with master password "my_master_password"
|
|
22
|
+
When I run `pws remove github` interactively
|
|
23
|
+
And I type "my_master_password_wrong"
|
|
24
|
+
Then the output should contain "Master password:"
|
|
25
|
+
And the output should contain "NO ACCESS"
|
|
26
|
+
|
|
27
|
+
|
|
@@ -0,0 +1,43 @@
|
|
|
1
|
+
Feature: Rename
|
|
2
|
+
In order to reorder my password safe
|
|
3
|
+
As a user
|
|
4
|
+
I want to rename passwords in my password safe
|
|
5
|
+
|
|
6
|
+
@slow-hack
|
|
7
|
+
Scenario: Rename the password entry "github" to "gh"
|
|
8
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
9
|
+
When I run `pws rename github gh` interactively
|
|
10
|
+
And I type "my_master_password"
|
|
11
|
+
Then the output should contain "Master password:"
|
|
12
|
+
And the output should contain "The password entry github has been renamed to gh"
|
|
13
|
+
When I run `pws show` interactively
|
|
14
|
+
And I type "my_master_password"
|
|
15
|
+
Then the output from "pws show" should contain "Master password:"
|
|
16
|
+
And the output from "pws show" should contain "Entries"
|
|
17
|
+
And the output from "pws show" should contain "gh"
|
|
18
|
+
And the output from "pws show" should not contain "github"
|
|
19
|
+
|
|
20
|
+
Scenario: Try to rename the password entry "github" to "gh" (but github does not exist)
|
|
21
|
+
Given A safe exists with master password "my_master_password"
|
|
22
|
+
When I run `pws rename github gh` interactively
|
|
23
|
+
And I type "my_master_password"
|
|
24
|
+
Then the output should contain "Master password:"
|
|
25
|
+
And the output should contain "No password found for github!"
|
|
26
|
+
|
|
27
|
+
Scenario: Try to rename the password entry "github" to "gh" (but gh already exists)
|
|
28
|
+
Given A safe exists with master password "my_master_password" and keys
|
|
29
|
+
| github | github_password |
|
|
30
|
+
| gh | gh_password |
|
|
31
|
+
When I run `pws rename github gh` interactively
|
|
32
|
+
And I type "my_master_password"
|
|
33
|
+
Then the output should contain "Master password:"
|
|
34
|
+
And the output should contain "There is already a password stored for gh. You need to remove it before naming another one gh!"
|
|
35
|
+
|
|
36
|
+
Scenario: Try to rename the password entry "github" to "gh" (but the master password is wrong)
|
|
37
|
+
Given A safe exists with master password "my_master_password"
|
|
38
|
+
When I run `pws rename github gh` interactively
|
|
39
|
+
And I type "my_master_password_wrong"
|
|
40
|
+
Then the output should contain "Master password:"
|
|
41
|
+
And the output should contain "NO ACCESS"
|
|
42
|
+
|
|
43
|
+
|
|
@@ -0,0 +1,37 @@
|
|
|
1
|
+
Feature: Show
|
|
2
|
+
In order to have an overview of my password safe
|
|
3
|
+
As a user
|
|
4
|
+
I want show a list of password entry keys
|
|
5
|
+
|
|
6
|
+
Scenario: Show the list
|
|
7
|
+
Given A safe exists with master password "my_master_password" and keys
|
|
8
|
+
| some | 123 |
|
|
9
|
+
| password | 345 |
|
|
10
|
+
| entries | 678 |
|
|
11
|
+
When I run `pws show` interactively
|
|
12
|
+
And I type "my_master_password"
|
|
13
|
+
Then the output should contain "Entries"
|
|
14
|
+
And the output should contain "some"
|
|
15
|
+
And the output should contain "password"
|
|
16
|
+
And the output should contain "entries"
|
|
17
|
+
|
|
18
|
+
Scenario: Show the list (but there is no entry yet)
|
|
19
|
+
Given A safe exists with master password "my_master_password"
|
|
20
|
+
When I run `pws show` interactively
|
|
21
|
+
And I type "my_master_password"
|
|
22
|
+
Then the output should contain "There aren't any passwords stored"
|
|
23
|
+
|
|
24
|
+
Scenario: Show the list ("pws" without show is an alias)
|
|
25
|
+
Given A safe exists with master password "my_master_password"
|
|
26
|
+
When I run `pws` interactively
|
|
27
|
+
And I type "my_master_password"
|
|
28
|
+
Then the output should contain "There aren't any passwords stored"
|
|
29
|
+
|
|
30
|
+
Scenario: Try to show the list (but the master password is wrong)
|
|
31
|
+
Given A safe exists with master password "my_master_password" and a key "github" with password "github_password"
|
|
32
|
+
When I run `pws show` interactively
|
|
33
|
+
And I type "my_master_password_wrong"
|
|
34
|
+
Then the output should contain "Master password:"
|
|
35
|
+
And the output should contain "NO ACCESS"
|
|
36
|
+
|
|
37
|
+
|
|
@@ -0,0 +1,36 @@
|
|
|
1
|
+
def create_safe(master, key_hash = {})
|
|
2
|
+
restore, $stdout = $stdout, StringIO.new # tmp silence $stdout
|
|
3
|
+
pws = PWS.new ENV["PWS"], nil, master
|
|
4
|
+
key_hash.each{ |key, password|
|
|
5
|
+
pws.add key, password
|
|
6
|
+
}
|
|
7
|
+
$stdout = restore
|
|
8
|
+
end
|
|
9
|
+
|
|
10
|
+
Given /^A safe exists with master password "([^"]*)"$/ do |master_password|
|
|
11
|
+
create_safe(master_password)
|
|
12
|
+
end
|
|
13
|
+
|
|
14
|
+
Given /^A safe exists with master password "([^"]*)" and a key "([^"]+)" with password "([^"]+)"$/ do |master_password, key, password|
|
|
15
|
+
create_safe(master_password, key => password)
|
|
16
|
+
end
|
|
17
|
+
|
|
18
|
+
Given /^A safe exists with master password "([^"]*)" and keys$/ do |master_password, key_table|
|
|
19
|
+
create_safe(master_password, key_table.rows_hash)
|
|
20
|
+
end
|
|
21
|
+
|
|
22
|
+
Given /^A clipboard content of "([^"]*)"$/ do |content|
|
|
23
|
+
Clipboard.copy content
|
|
24
|
+
end
|
|
25
|
+
|
|
26
|
+
Then /^the clipboard should contain "([^"]*)"$/ do |password|
|
|
27
|
+
password.should == Clipboard.paste
|
|
28
|
+
end
|
|
29
|
+
|
|
30
|
+
Then /^the clipboard should match \/([^\/]*)\/$/ do |expected|
|
|
31
|
+
assert_matching_output(expected, Clipboard.paste)
|
|
32
|
+
end
|
|
33
|
+
|
|
34
|
+
Then /^the clipboard should match ([^\/].+)$/ do |expected|
|
|
35
|
+
assert_matching_output(expected, Clipboard.paste)
|
|
36
|
+
end
|
|
@@ -0,0 +1,41 @@
|
|
|
1
|
+
require "bundler/setup"
|
|
2
|
+
require 'aruba/cucumber'
|
|
3
|
+
require 'clipboard'
|
|
4
|
+
require 'securerandom'
|
|
5
|
+
require 'fileutils'
|
|
6
|
+
require_relative '../../lib/pws'
|
|
7
|
+
|
|
8
|
+
# Make sure bin is available
|
|
9
|
+
|
|
10
|
+
ENV['PATH'] = "#{File.expand_path(File.dirname(__FILE__) + '/../../bin')}#{File::PATH_SEPARATOR}#{ENV['PATH']}"
|
|
11
|
+
|
|
12
|
+
# Hooks
|
|
13
|
+
|
|
14
|
+
BEGIN{
|
|
15
|
+
$original_pws_file = ENV["PWS"]
|
|
16
|
+
}
|
|
17
|
+
|
|
18
|
+
END{
|
|
19
|
+
Clipboard.clear
|
|
20
|
+
ENV["PWS"] = $original_pws_file
|
|
21
|
+
}
|
|
22
|
+
|
|
23
|
+
Around do |_, block|
|
|
24
|
+
# NOTE: You cannot parallelize the tests, because they use the clipboard and the env var...
|
|
25
|
+
Clipboard.clear
|
|
26
|
+
ENV["PWS"] = File.expand_path('pws-test-' + SecureRandom.uuid)
|
|
27
|
+
|
|
28
|
+
block.call
|
|
29
|
+
|
|
30
|
+
FileUtils.rm ENV["PWS"] if File.exist? ENV["PWS"]
|
|
31
|
+
end
|
|
32
|
+
|
|
33
|
+
# Hacks
|
|
34
|
+
|
|
35
|
+
Before('@slow-hack') do
|
|
36
|
+
@aruba_io_wait_seconds = 0.5
|
|
37
|
+
end
|
|
38
|
+
|
|
39
|
+
Before('@wait-11s') do
|
|
40
|
+
@aruba_timeout_seconds = 11
|
|
41
|
+
end
|
data/lib/pws.rb
CHANGED
|
@@ -128,7 +128,15 @@ class PWS
|
|
|
128
128
|
|
|
129
129
|
# Changes the master password
|
|
130
130
|
def master(password = nil)
|
|
131
|
-
|
|
131
|
+
if !password
|
|
132
|
+
new_password = ask_for_password(%[please enter the new master password], :yellow, :bold)
|
|
133
|
+
password = ask_for_password(%[please enter the new master password, again], :yellow, :bold)
|
|
134
|
+
if new_password != password
|
|
135
|
+
pa %[The passwords don't match!], :red
|
|
136
|
+
return false
|
|
137
|
+
end
|
|
138
|
+
end
|
|
139
|
+
@pw_hash = Encryptor.hash(password)
|
|
132
140
|
write_safe
|
|
133
141
|
pa %[The master password has been changed], :green
|
|
134
142
|
return true
|
data/lib/pws/version.rb
CHANGED
data/pws.gemspec
CHANGED
|
@@ -12,11 +12,11 @@ Gem::Specification.new do |s|
|
|
|
12
12
|
s.homepage = 'https://github.com/janlelis/pws'
|
|
13
13
|
s.summary = "pws is a cli password safe."
|
|
14
14
|
s.description = "pws is a command-line password safe. Please run `pws help` for usage information."
|
|
15
|
-
s.files = Dir.glob(%w[{lib,test}/**/*.rb bin/* [A-Z]*.{txt,rdoc} ext/**/*.{rb,c}]) + %w{Rakefile pws.gemspec}
|
|
16
|
-
s.extra_rdoc_files = ["README", "LICENSE"]
|
|
15
|
+
s.files = Dir.glob(%w[{lib,test}/**/*.rb bin/* [A-Z]*.{txt,rdoc} ext/**/*.{rb,c} features/**/*]) + %w{Rakefile pws.gemspec}
|
|
16
|
+
s.extra_rdoc_files = ["README.md", "LICENSE"]
|
|
17
17
|
s.license = 'MIT'
|
|
18
18
|
s.executables = ['pws']
|
|
19
|
-
s.add_dependency 'clipboard', '~> 1.0.
|
|
19
|
+
s.add_dependency 'clipboard', '~> 1.0.1'
|
|
20
20
|
s.add_dependency 'zucker', '>= 12.1'
|
|
21
21
|
s.add_dependency 'paint', '>= 0.8.4'
|
|
22
22
|
s.add_development_dependency 'rake'
|
metadata
CHANGED
|
@@ -1,7 +1,7 @@
|
|
|
1
1
|
--- !ruby/object:Gem::Specification
|
|
2
2
|
name: pws
|
|
3
3
|
version: !ruby/object:Gem::Version
|
|
4
|
-
version: 0.9.
|
|
4
|
+
version: 0.9.1
|
|
5
5
|
prerelease:
|
|
6
6
|
platform: ruby
|
|
7
7
|
authors:
|
|
@@ -9,22 +9,22 @@ authors:
|
|
|
9
9
|
autorequire:
|
|
10
10
|
bindir: bin
|
|
11
11
|
cert_chain: []
|
|
12
|
-
date: 2012-01-
|
|
12
|
+
date: 2012-01-24 00:00:00.000000000 Z
|
|
13
13
|
dependencies:
|
|
14
14
|
- !ruby/object:Gem::Dependency
|
|
15
15
|
name: clipboard
|
|
16
|
-
requirement: &
|
|
16
|
+
requirement: &13917980 !ruby/object:Gem::Requirement
|
|
17
17
|
none: false
|
|
18
18
|
requirements:
|
|
19
19
|
- - ~>
|
|
20
20
|
- !ruby/object:Gem::Version
|
|
21
|
-
version: 1.0.
|
|
21
|
+
version: 1.0.1
|
|
22
22
|
type: :runtime
|
|
23
23
|
prerelease: false
|
|
24
|
-
version_requirements: *
|
|
24
|
+
version_requirements: *13917980
|
|
25
25
|
- !ruby/object:Gem::Dependency
|
|
26
26
|
name: zucker
|
|
27
|
-
requirement: &
|
|
27
|
+
requirement: &13916940 !ruby/object:Gem::Requirement
|
|
28
28
|
none: false
|
|
29
29
|
requirements:
|
|
30
30
|
- - ! '>='
|
|
@@ -32,10 +32,10 @@ dependencies:
|
|
|
32
32
|
version: '12.1'
|
|
33
33
|
type: :runtime
|
|
34
34
|
prerelease: false
|
|
35
|
-
version_requirements: *
|
|
35
|
+
version_requirements: *13916940
|
|
36
36
|
- !ruby/object:Gem::Dependency
|
|
37
37
|
name: paint
|
|
38
|
-
requirement: &
|
|
38
|
+
requirement: &13887320 !ruby/object:Gem::Requirement
|
|
39
39
|
none: false
|
|
40
40
|
requirements:
|
|
41
41
|
- - ! '>='
|
|
@@ -43,10 +43,10 @@ dependencies:
|
|
|
43
43
|
version: 0.8.4
|
|
44
44
|
type: :runtime
|
|
45
45
|
prerelease: false
|
|
46
|
-
version_requirements: *
|
|
46
|
+
version_requirements: *13887320
|
|
47
47
|
- !ruby/object:Gem::Dependency
|
|
48
48
|
name: rake
|
|
49
|
-
requirement: &
|
|
49
|
+
requirement: &13886440 !ruby/object:Gem::Requirement
|
|
50
50
|
none: false
|
|
51
51
|
requirements:
|
|
52
52
|
- - ! '>='
|
|
@@ -54,10 +54,10 @@ dependencies:
|
|
|
54
54
|
version: '0'
|
|
55
55
|
type: :development
|
|
56
56
|
prerelease: false
|
|
57
|
-
version_requirements: *
|
|
57
|
+
version_requirements: *13886440
|
|
58
58
|
- !ruby/object:Gem::Dependency
|
|
59
59
|
name: cucumber
|
|
60
|
-
requirement: &
|
|
60
|
+
requirement: &13885760 !ruby/object:Gem::Requirement
|
|
61
61
|
none: false
|
|
62
62
|
requirements:
|
|
63
63
|
- - ! '>='
|
|
@@ -65,10 +65,10 @@ dependencies:
|
|
|
65
65
|
version: '0'
|
|
66
66
|
type: :development
|
|
67
67
|
prerelease: false
|
|
68
|
-
version_requirements: *
|
|
68
|
+
version_requirements: *13885760
|
|
69
69
|
- !ruby/object:Gem::Dependency
|
|
70
70
|
name: aruba
|
|
71
|
-
requirement: &
|
|
71
|
+
requirement: &13885120 !ruby/object:Gem::Requirement
|
|
72
72
|
none: false
|
|
73
73
|
requirements:
|
|
74
74
|
- - ! '>='
|
|
@@ -76,7 +76,7 @@ dependencies:
|
|
|
76
76
|
version: '0'
|
|
77
77
|
type: :development
|
|
78
78
|
prerelease: false
|
|
79
|
-
version_requirements: *
|
|
79
|
+
version_requirements: *13885120
|
|
80
80
|
description: pws is a command-line password safe. Please run `pws help` for usage
|
|
81
81
|
information.
|
|
82
82
|
email: mail@janlelis.de
|
|
@@ -84,16 +84,28 @@ executables:
|
|
|
84
84
|
- pws
|
|
85
85
|
extensions: []
|
|
86
86
|
extra_rdoc_files:
|
|
87
|
-
- README
|
|
87
|
+
- README.md
|
|
88
88
|
- LICENSE
|
|
89
89
|
files:
|
|
90
90
|
- lib/pws/encryptor.rb
|
|
91
91
|
- lib/pws/version.rb
|
|
92
92
|
- lib/pws.rb
|
|
93
93
|
- bin/pws
|
|
94
|
+
- features/step_definitions/pws_steps.rb
|
|
95
|
+
- features/remove.feature
|
|
96
|
+
- features/namespaces.feature
|
|
97
|
+
- features/generate.feature
|
|
98
|
+
- features/rename.feature
|
|
99
|
+
- features/show.feature
|
|
100
|
+
- features/add.feature
|
|
101
|
+
- features/access.feature
|
|
102
|
+
- features/master.feature
|
|
103
|
+
- features/get.feature
|
|
104
|
+
- features/support/env.rb
|
|
105
|
+
- features/misc.feature
|
|
94
106
|
- Rakefile
|
|
95
107
|
- pws.gemspec
|
|
96
|
-
- README
|
|
108
|
+
- README.md
|
|
97
109
|
- LICENSE
|
|
98
110
|
homepage: https://github.com/janlelis/pws
|
|
99
111
|
licenses:
|
data/README
DELETED
|
@@ -1,13 +0,0 @@
|
|
|
1
|
-
pws is a command-line password safe/manager written in Ruby. Install it with
|
|
2
|
-
|
|
3
|
-
$ gem install pws
|
|
4
|
-
|
|
5
|
-
Please run `pws help` for usage information.
|
|
6
|
-
|
|
7
|
-
Trust the code by reading the source! Originally based on: http://rbjl.net/41-tutorial-build-your-own-password-safe-with-ruby
|
|
8
|
-
|
|
9
|
-
Cucumber specs loosely based on https://github.com/thecatwasnot/passwordsafe/blob/master/features/add.feature by thecatwasnot - thanks.
|
|
10
|
-
|
|
11
|
-
Copyright: 2010-2012 Jan Lelis, MIT-LICENSE
|
|
12
|
-
|
|
13
|
-
J-_-L
|