eva-exploit 2.5__tar.gz
This diff represents the content of publicly available package versions that have been released to one of the supported registries. The information contained in this diff is provided for informational purposes only and reflects changes between package versions as they appear in their respective public registries.
- eva_exploit-2.5/PKG-INFO +410 -0
- eva_exploit-2.5/README.md +398 -0
- eva_exploit-2.5/config.py +29 -0
- eva_exploit-2.5/eva.py +166 -0
- eva_exploit-2.5/eva_exploit.egg-info/PKG-INFO +410 -0
- eva_exploit-2.5/eva_exploit.egg-info/SOURCES.txt +20 -0
- eva_exploit-2.5/eva_exploit.egg-info/dependency_links.txt +1 -0
- eva_exploit-2.5/eva_exploit.egg-info/entry_points.txt +2 -0
- eva_exploit-2.5/eva_exploit.egg-info/requires.txt +3 -0
- eva_exploit-2.5/eva_exploit.egg-info/top_level.txt +5 -0
- eva_exploit-2.5/modules/__init__.py +0 -0
- eva_exploit-2.5/modules/attack_map.py +467 -0
- eva_exploit-2.5/modules/llm.py +599 -0
- eva_exploit-2.5/modules/prompt_builder.py +56 -0
- eva_exploit-2.5/modules/reporting.py +254 -0
- eva_exploit-2.5/pyproject.toml +29 -0
- eva_exploit-2.5/sessions/__init__.py +0 -0
- eva_exploit-2.5/sessions/eva_session.py +457 -0
- eva_exploit-2.5/setup.cfg +4 -0
- eva_exploit-2.5/utils/__init__.py +0 -0
- eva_exploit-2.5/utils/system.py +264 -0
- eva_exploit-2.5/utils/ui.py +191 -0
eva_exploit-2.5/PKG-INFO
ADDED
|
@@ -0,0 +1,410 @@
|
|
|
1
|
+
Metadata-Version: 2.4
|
|
2
|
+
Name: eva-exploit
|
|
3
|
+
Version: 2.5
|
|
4
|
+
Summary: Exploit Vector Agent
|
|
5
|
+
Author: ARCANGEL0
|
|
6
|
+
License: MIT
|
|
7
|
+
Requires-Python: >=3.10
|
|
8
|
+
Description-Content-Type: text/markdown
|
|
9
|
+
Requires-Dist: colorama>=0.4.6
|
|
10
|
+
Requires-Dist: openai>=1.0.0
|
|
11
|
+
Requires-Dist: requests>=2.31.0
|
|
12
|
+
|
|
13
|
+

|
|
14
|
+
|
|
15
|
+
<div align="center">
|
|
16
|
+
|
|
17
|
+
# ⫻ 𝝣.𝗩.𝝠
|
|
18
|
+
## ⮡ Exploit Vector Agent
|
|
19
|
+
<br>
|
|
20
|
+
|
|
21
|
+
**Autonomous offensive security AI for guiding pentest processes**
|
|
22
|
+
|
|
23
|
+
[](https://github.com/ARCANGEL0/EVA)
|
|
24
|
+
[](https://github.com/ARCANGEL0/EVA)
|
|
25
|
+
[](https://github.com/ARCANGEL0/EVA/fork)
|
|
26
|
+
[](https://github.com/ARCANGEL0/EVA)
|
|
27
|
+
|
|
28
|
+
[](LICENSE)
|
|
29
|
+
[](#)
|
|
30
|
+
[](#)
|
|
31
|
+
|
|
32
|
+

|
|
33
|
+

|
|
34
|
+

|
|
35
|
+

|
|
36
|
+
|
|
37
|
+
</div>
|
|
38
|
+
|
|
39
|
+
---
|
|
40
|
+
|
|
41
|
+
## 𝝺 Overview
|
|
42
|
+
|
|
43
|
+
**EVA** is an AI penetration testing agent that guides users through complete pentest engagements with AI-powered attack strategy, autonomous command generation, and real-time vulnerability analysis based on outputs. The goal is not to replace the pentest professional but to guide and assist and provide faster results.
|
|
44
|
+
|
|
45
|
+
### Main funcionalities
|
|
46
|
+
|
|
47
|
+
- **🜂 Intelligent Reasoning**: Advanced AI-driven analysis and attack path identification depending on query.
|
|
48
|
+
- **ⵢ Automated Enumeration**: Systematic target reconnaissance and information gathering based on provided target.
|
|
49
|
+
- **ꎈ Vulnerability Assessment**: AI-powered vulnerability identification and exploitation strategies, suggesting next steps for vulnerability or OSINT.
|
|
50
|
+
- **⑇ Multiple AI Backends**: Support for Ollama, OpenAI GPT, Anthropic, Gemini, G4F.dev and custom API endpoints
|
|
51
|
+
- **ㄖ Session Management**: Persistent sessions and chats
|
|
52
|
+
- **⑅ Interactive Interface**: Real-time command execution and analysis of output in multi-stage.
|
|
53
|
+
|
|
54
|
+
---
|
|
55
|
+
|
|
56
|
+
|
|
57
|
+
## ⵢ EVA Logic & Pentest Process Flow
|
|
58
|
+
|
|
59
|
+
```mermaid
|
|
60
|
+
graph TD
|
|
61
|
+
|
|
62
|
+
A[🜂 EVA Launch] --> B{🢧 Session Selection}
|
|
63
|
+
B -->|Existing Session| C[🢧 Load Session Data]
|
|
64
|
+
B -->|New Session| D[߭ Initialize Session]
|
|
65
|
+
C --> E[ㄖ Select AI Backend]
|
|
66
|
+
D --> E
|
|
67
|
+
|
|
68
|
+
E --> F[🦙 Ollama Local]
|
|
69
|
+
E --> G[⬡ OpenAI GPT]
|
|
70
|
+
E --> J1[✶ Anthropic Claude]
|
|
71
|
+
E --> J2[✦ Google Gemini]
|
|
72
|
+
E --> H[⟅ Custom API]
|
|
73
|
+
E --> I[🜅 G4F.dev Provider]
|
|
74
|
+
|
|
75
|
+
F --> J[Pentest Shell]
|
|
76
|
+
G --> J
|
|
77
|
+
J1 --> J
|
|
78
|
+
J2 --> J
|
|
79
|
+
H --> J
|
|
80
|
+
I --> J
|
|
81
|
+
|
|
82
|
+
J --> K[⌖ Target Definition]
|
|
83
|
+
K --> L[🧠 AI Pentest Strategy]
|
|
84
|
+
|
|
85
|
+
L --> M[🝯 Reconnaissance Phase]
|
|
86
|
+
M --> N[➤_ Execute Commands]
|
|
87
|
+
N --> O[ꎐ Analyze Results]
|
|
88
|
+
O --> P{ᐈ Vulnerabilities Found?}
|
|
89
|
+
|
|
90
|
+
P -->|Yes| Q[🖧 Exploitation Planning]
|
|
91
|
+
P -->|No| R[⭯ More Enumeration]
|
|
92
|
+
R --> L
|
|
93
|
+
|
|
94
|
+
Q --> S[⚡ Exploitation Phase]
|
|
95
|
+
Q --> T[Export graphs and mapped networks
|
|
96
|
+
- IN DEVELOPMENT -]
|
|
97
|
+
|
|
98
|
+
S --> U[➤_ Execute Exploit]
|
|
99
|
+
U --> V{🞜 Access Gained?}
|
|
100
|
+
|
|
101
|
+
V -->|Yes| W[𐱃 Privilege Escalation]
|
|
102
|
+
V -->|Failed| X[⭯ Alternative Methods]
|
|
103
|
+
X --> Q
|
|
104
|
+
|
|
105
|
+
W --> Y[𐦝 Post-Exploitation]
|
|
106
|
+
Y --> Z{🞜 Objectives Met?}
|
|
107
|
+
|
|
108
|
+
Z -->|Generate Report| AA[📋 Generate Report
|
|
109
|
+
- IN DEVELOPMENT -]
|
|
110
|
+
Z -->|Exit and Save| AB[💾 Save & Exit]
|
|
111
|
+
Z -->|No| AC[🔍 Continue Pentest]
|
|
112
|
+
AC --> L
|
|
113
|
+
|
|
114
|
+
AA --> AB
|
|
115
|
+
|
|
116
|
+
subgraph "🍎 EVA "
|
|
117
|
+
AD[⯐ Attack Strategy AI]
|
|
118
|
+
AE[𝚵 Session Memory]
|
|
119
|
+
AF[ᐮ Vulnerability Analysis]
|
|
120
|
+
AG[CVE DATABASE SEARCH
|
|
121
|
+
- IN DEVELOPMENT -]
|
|
122
|
+
AH[𐰬 Output Processing]
|
|
123
|
+
end
|
|
124
|
+
|
|
125
|
+
L --> AD
|
|
126
|
+
AD --> AE
|
|
127
|
+
O --> AF
|
|
128
|
+
AF --> AG
|
|
129
|
+
AG --> AH
|
|
130
|
+
AH --> L
|
|
131
|
+
```
|
|
132
|
+
|
|
133
|
+
---
|
|
134
|
+
|
|
135
|
+
<details>
|
|
136
|
+
<summary><h2>➤ Quick Start</h2></summary>
|
|
137
|
+
|
|
138
|
+
### 🍎 Installation
|
|
139
|
+
|
|
140
|
+
```bash
|
|
141
|
+
# Ollama for local endpoint (optional)
|
|
142
|
+
curl -fsSL https://ollama.ai/install.sh | shr
|
|
143
|
+
|
|
144
|
+
# pip installation
|
|
145
|
+
pip install eva-exploit
|
|
146
|
+
eva
|
|
147
|
+
|
|
148
|
+
# EVA installation
|
|
149
|
+
git clone https://github.com/ARCANGEL0/EVA.git
|
|
150
|
+
cd EVA
|
|
151
|
+
chmod +x eva.py
|
|
152
|
+
./eva.py
|
|
153
|
+
|
|
154
|
+
# Adding it to PATH to be acessible anywhere
|
|
155
|
+
sudo mv eva.py /usr/local/bin/eva
|
|
156
|
+
```
|
|
157
|
+
|
|
158
|
+
### ⬢ Configuring EVA.
|
|
159
|
+
|
|
160
|
+
When starting EVA, it will automatically handle:
|
|
161
|
+
- ✅ OpenAI API key setup (if using GPT backend)
|
|
162
|
+
- ✅ Ollama model download (WhiteRabbit-Neo, feel free to change to any other desired model)
|
|
163
|
+
- ✅ Session directory creation
|
|
164
|
+
- ✅ Dependencies installation
|
|
165
|
+
|
|
166
|
+
<strong> If you wish to modify endpoints, ollama models or other: you can find these options in `config.py` </strong>
|
|
167
|
+
|
|
168
|
+
> EVA is now modular, with a root launcher and separate folders for logic/components.
|
|
169
|
+
|
|
170
|
+
### 📁 Directory Structure of EVA
|
|
171
|
+
|
|
172
|
+
```
|
|
173
|
+
~/.config/eva/
|
|
174
|
+
├── sessions/ # Session storage
|
|
175
|
+
│ ├── session1.json
|
|
176
|
+
│ ├── session2.json
|
|
177
|
+
│ └── ...
|
|
178
|
+
└── .env # API keys (auto-generated)
|
|
179
|
+
```
|
|
180
|
+
|
|
181
|
+
### ꀬ Where to change EVA options
|
|
182
|
+
|
|
183
|
+
```python
|
|
184
|
+
# Key Configuration Options
|
|
185
|
+
API_ENDPOINT = "" # This is the custom API URL.
|
|
186
|
+
G4F_MODEL = "gpt-5-1-instant"
|
|
187
|
+
OLLAMA_MODEL = "jimscard/whiterabbit-neo:latest" # change ollama model as you wish, most recommended one is whiterabbit
|
|
188
|
+
ANTHROPIC_MODEL = "claude-3-5-sonnet-latest"
|
|
189
|
+
GEMINI_MODEL = "gemini-2.0-flash"
|
|
190
|
+
CONFIG_DIR = Path.home() / ".config" / "eva" # config folder for EVA
|
|
191
|
+
SESSIONS_DIR = CONFIG_DIR / "sessions" # where to store EVA sessions
|
|
192
|
+
REPORTS_DIR = CONFIG_DIR / "reports" # generated reports
|
|
193
|
+
MAPS_DIR = CONFIG_DIR / "attack_maps" # generated visual attack maps
|
|
194
|
+
```
|
|
195
|
+
|
|
196
|
+
</details>
|
|
197
|
+
|
|
198
|
+
<details>
|
|
199
|
+
<summary><h2>🖴 Usage Guide</h2></summary>
|
|
200
|
+
|
|
201
|
+
### Initialization
|
|
202
|
+
|
|
203
|
+
```bash
|
|
204
|
+
python3 eva.py
|
|
205
|
+
# or if installed via pip:
|
|
206
|
+
eva
|
|
207
|
+
```
|
|
208
|
+
|
|
209
|
+
1. **Select Session**: Choose existing session or create new one
|
|
210
|
+
2. **Choose AI Backend**:
|
|
211
|
+
- **Ollama** (Recommended): Local AI with WhiteRabbit-Neo model
|
|
212
|
+
- **GPT-5**: OpenAI's latest model (requires API key)
|
|
213
|
+
- **G4F**: Uses g4f.dev endpoints with model GPT 5-1, feel free to change model used.
|
|
214
|
+
- **Anthropic**: Claude API backend (requires API key)
|
|
215
|
+
- **Gemini**: Google Gemini API backend (requires API key)
|
|
216
|
+
- **Custom API**: Your own API endpoint if desired
|
|
217
|
+
3. In the input field of chat, type in your request or what you need assistance with for EVA to help you!
|
|
218
|
+
|
|
219
|
+
> USER > i need help with a CTF machine, ip is 10.10.16.81
|
|
220
|
+
|
|
221
|
+
### After making a request, commands will be provided and the pentest workflow will start, use commands below as reference.
|
|
222
|
+
|
|
223
|
+
| Command | Description |
|
|
224
|
+
|---------|-------------|
|
|
225
|
+
| `/exit` / `/quit` | Exit EVA and save session |
|
|
226
|
+
| `/model` | Change AI backend |
|
|
227
|
+
| `/rename` | Rename the current session |
|
|
228
|
+
| `/menu` | Return to session menu |
|
|
229
|
+
| `R` | Run suggested command |
|
|
230
|
+
| `S` | Skip command |
|
|
231
|
+
| `A` | Ask for next step |
|
|
232
|
+
| `Q` | Quit session |
|
|
233
|
+
|
|
234
|
+
### ㄖ Example of chat session
|
|
235
|
+
|
|
236
|
+
> demonstration video.
|
|
237
|
+
|
|
238
|
+
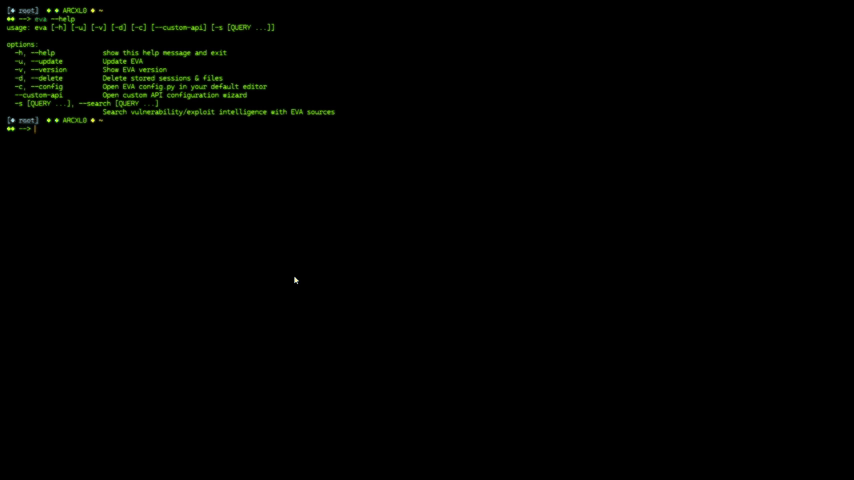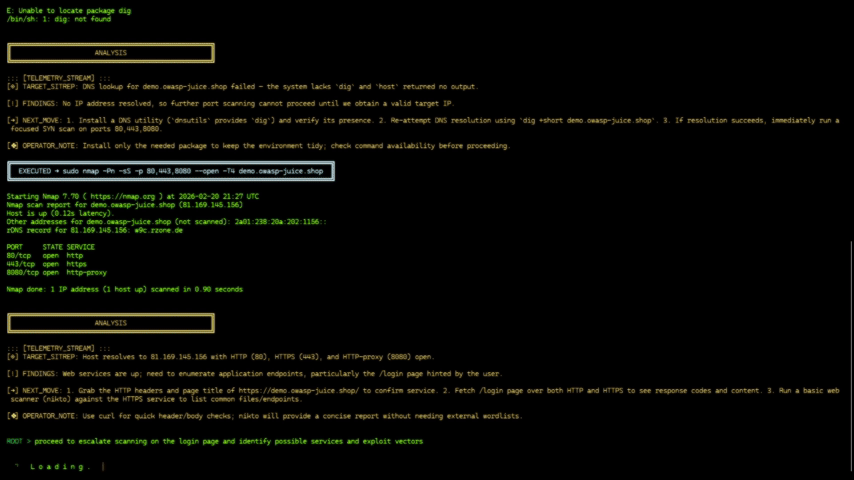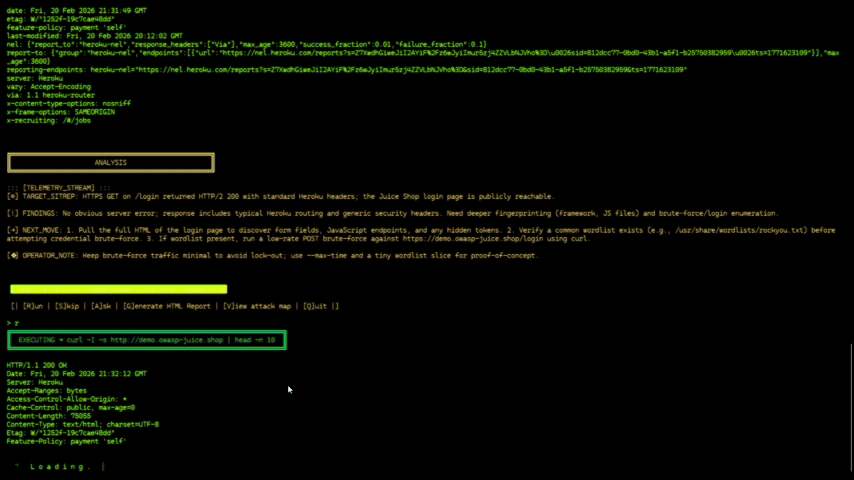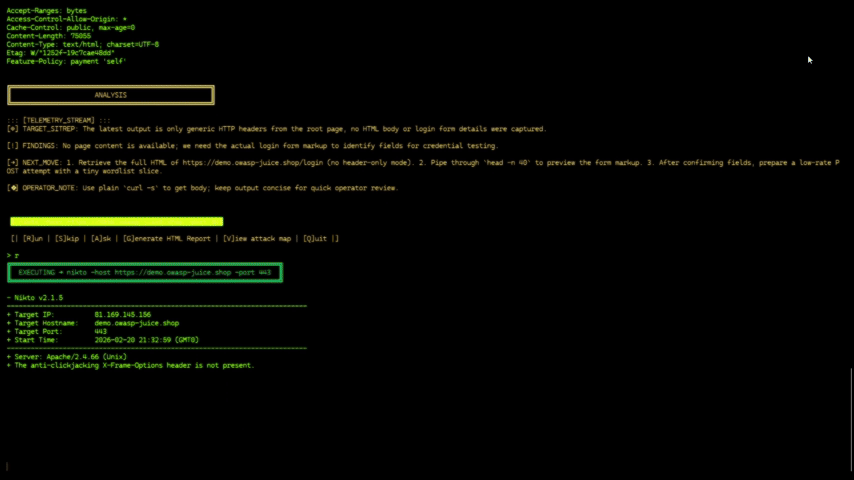
|
|
239
|
+
|
|
240
|
+
|
|
241
|
+
```
|
|
242
|
+
USER > I'm on a Windows target at IP 10.10.11.95, what should I enumerate first?
|
|
243
|
+
|
|
244
|
+
[ANALYSIS]
|
|
245
|
+
Based on the Windows environment, I need to perform comprehensive
|
|
246
|
+
enumeration focusing on:
|
|
247
|
+
|
|
248
|
+
1. System Information (OS version, patches, architecture)
|
|
249
|
+
2. Network Services (ports, services, listening processes)
|
|
250
|
+
3. User Context (current user, groups, privileges)
|
|
251
|
+
4. Security Controls (AV, firewall, UAC settings)
|
|
252
|
+
5. Potential Attack Vectors (SMB, RDP, IIS, etc.)
|
|
253
|
+
|
|
254
|
+
Let me start with basic system reconnaissance to understand the target better...
|
|
255
|
+
|
|
256
|
+
> execute: nmap -sC -sV -O 10.10.10.10
|
|
257
|
+
| [R]un | [S]kip | [A]sk | [G]enerate HTML Report | [V]iew attack map | [Q]uit |
|
|
258
|
+
|
|
259
|
+
> R
|
|
260
|
+
```
|
|
261
|
+
|
|
262
|
+
</details>
|
|
263
|
+
|
|
264
|
+
|
|
265
|
+
<details>
|
|
266
|
+
<summary><h2>Ξ AI Backends</h2></summary>
|
|
267
|
+
|
|
268
|
+
### 🦙 Ollama (Recommended)
|
|
269
|
+
- **Model**: `jimscard/whiterabbit-neo:latest` (best one for OffSec)
|
|
270
|
+
- ✅ Complete offline operation
|
|
271
|
+
- ✅ No API costs
|
|
272
|
+
- ✅ Privacy-focused
|
|
273
|
+
- ❌ Higher CPU/GPU usage, recommended for machines above 16GB VRAM/RAM
|
|
274
|
+
- ❌ Heavier model, ~9.8gb model
|
|
275
|
+
|
|
276
|
+
### ⬡ OpenAI GPT
|
|
277
|
+
- **Models**: GPT-5, GPT-4.1 (fallback)
|
|
278
|
+
- **About**:
|
|
279
|
+
- ✅ Faster reasoning
|
|
280
|
+
- ✅ Extensive knowledge base
|
|
281
|
+
- ✅ Continuous updates
|
|
282
|
+
- ❌ Paid, requires apikey
|
|
283
|
+
|
|
284
|
+
### ᛃ G4F.dev
|
|
285
|
+
- **Models**: GPT-5-1
|
|
286
|
+
- **About**:
|
|
287
|
+
- ✅ Updated information in real-time (usually)
|
|
288
|
+
- ✅ Quick responses
|
|
289
|
+
- ❌ Might be unstable or down sometimes, low stability.
|
|
290
|
+
|
|
291
|
+
### ⟅ Custom API
|
|
292
|
+
- **Endpoint**: Configurable in `API_ENDPOINT` to use your own as you wish.
|
|
293
|
+
- **About**:
|
|
294
|
+
- ✅ Custom model integration
|
|
295
|
+
- ✅ Modifiable as you wish
|
|
296
|
+
|
|
297
|
+
#### More backends compability will be provided soon!
|
|
298
|
+
|
|
299
|
+
### ✶ Anthropic
|
|
300
|
+
- **Model**: Configurable via `ANTHROPIC_MODEL`
|
|
301
|
+
- **About**:
|
|
302
|
+
- ✅ Strong reasoning quality
|
|
303
|
+
- ✅ Stable commercial API
|
|
304
|
+
- ❌ Requires `ANTHROPIC_API_KEY`
|
|
305
|
+
|
|
306
|
+
### ✦ Gemini
|
|
307
|
+
- **Model**: Configurable via `GEMINI_MODEL`
|
|
308
|
+
- **About**:
|
|
309
|
+
- ✅ Fast response latency
|
|
310
|
+
- ✅ Native JSON output mode
|
|
311
|
+
- ❌ Requires `GEMINI_API_KEY`
|
|
312
|
+
|
|
313
|
+
</details>
|
|
314
|
+
|
|
315
|
+
<details>
|
|
316
|
+
<summary><h2>⑇ Roadmap</h2></summary>
|
|
317
|
+
|
|
318
|
+
- [x] **⬢ OpenAI integration**: Integrated OpenAI into EVA
|
|
319
|
+
- [x] **⬢ G4F.DEV**: Added G4F endpoints to free GPT5 usage.
|
|
320
|
+
- [x] **⬢ Custom API**: Add custom endpoint besides ollama and OpenAI
|
|
321
|
+
- [x] **⬡ Automated Reporting**: Concise HTML report generation (+ optional PDF via wkhtmltopdf)
|
|
322
|
+
- [ ] **⬡ Cloud Integration**: AWS/GCP deployment ready
|
|
323
|
+
- [ ] **⬡ CVE Database Integration**: Real-time vulnerability data
|
|
324
|
+
- [ ] **⬡ Web Interface**: Browser-based EVA dashboard
|
|
325
|
+
- [ ] **⬡ Visual Attack Maps**: Interactive network diagrams such as connections or such, like Kerberos domains and AD devices.
|
|
326
|
+
|
|
327
|
+
</details>
|
|
328
|
+
|
|
329
|
+
|
|
330
|
+
<details>
|
|
331
|
+
<summary><h2>⨹ Legal Notice</h2></summary>
|
|
332
|
+
|
|
333
|
+
### 🚨 IMPORTANT
|
|
334
|
+
|
|
335
|
+
### This tool is for allowed environment only!
|
|
336
|
+
|
|
337
|
+
#### ✅ APPROVED USE CASES
|
|
338
|
+
> CTF (Capture The Flag) competitions <br>
|
|
339
|
+
> Authorized penetration testing <br>
|
|
340
|
+
> Security research and laboratory environments <br>
|
|
341
|
+
> Systems you own or have explicit permission to test <br>
|
|
342
|
+
|
|
343
|
+
#### 🚫 PROHIBITED USE
|
|
344
|
+
> Unauthorized access to any system <br>
|
|
345
|
+
> Illegal or malicious activities <br>
|
|
346
|
+
> Production systems without explicit authorization <br>
|
|
347
|
+
> Networks you do not own or control
|
|
348
|
+
|
|
349
|
+
### ⚠️ DISCLAIMER
|
|
350
|
+
```
|
|
351
|
+
I take no responsibility for misuse, illegal activity, or unauthorized use.
|
|
352
|
+
Any and all consequences are the sole responsibility of the user.
|
|
353
|
+
```
|
|
354
|
+
|
|
355
|
+
</details>
|
|
356
|
+
|
|
357
|
+
|
|
358
|
+
<details>
|
|
359
|
+
<summary><h2>⫻ License</h2></summary>
|
|
360
|
+
|
|
361
|
+
### MIT License
|
|
362
|
+
|
|
363
|
+
```
|
|
364
|
+
MIT License
|
|
365
|
+
|
|
366
|
+
Copyright (c) 2025 EVA - Exploit Vector Agent
|
|
367
|
+
|
|
368
|
+
Permission is hereby granted, free of charge, to any person obtaining a copy
|
|
369
|
+
of this software and associated documentation files (the "Software"), to deal
|
|
370
|
+
in the Software without restriction, including without limitation the rights
|
|
371
|
+
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
|
372
|
+
copies of the Software, and to permit persons to whom the Software is
|
|
373
|
+
furnished to do so, subject to the following conditions:
|
|
374
|
+
|
|
375
|
+
The above copyright notice and this permission notice shall be included in all
|
|
376
|
+
copies or substantial portions of the Software.
|
|
377
|
+
|
|
378
|
+
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
|
379
|
+
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
|
380
|
+
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
|
381
|
+
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
|
382
|
+
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
|
383
|
+
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
|
384
|
+
SOFTWARE.
|
|
385
|
+
```
|
|
386
|
+
|
|
387
|
+
</details>
|
|
388
|
+
|
|
389
|
+
<div align="center">
|
|
390
|
+
|
|
391
|
+
## ❤️ Support
|
|
392
|
+
|
|
393
|
+
### if you enjoy the project and want to support future development:
|
|
394
|
+
|
|
395
|
+
[](https://github.com/ARCANGEL0/EVA)
|
|
396
|
+
[](https://github.com/ARCANGEL0)
|
|
397
|
+
<br>
|
|
398
|
+
|
|
399
|
+
<a href='https://ko-fi.com/J3J7WTYV7' target='_blank'><img height='36' style='border:0px;height:36px;' src='https://storage.ko-fi.com/cdn/kofi3.png?v=6' border='0' alt='Buy Me a Coffee at ko-fi.com' /></a>
|
|
400
|
+
<br>
|
|
401
|
+
<strong>Hack the world. Byte by Byte.</strong> ⛛ <br>
|
|
402
|
+
𝝺𝗿𝗰𝗮𝗻𝗴𝗲𝗹𝗼 @ 2025
|
|
403
|
+
|
|
404
|
+
**[[ꋧ]](#-𝝣𝗩𝝠)**
|
|
405
|
+
|
|
406
|
+
</div>
|
|
407
|
+
|
|
408
|
+
---
|
|
409
|
+
|
|
410
|
+
*⚠️ Remember: With great power comes great responsibility. Use this tool ethically and legally.*
|