puppet-check 1.5.1 → 1.6.0
This diff represents the content of publicly available package versions that have been released to one of the supported registries. The information contained in this diff is provided for informational purposes only and reflects changes between package versions as they appear in their respective public registries.
- checksums.yaml +5 -5
- data/CHANGELOG.md +7 -0
- data/README.md +20 -25
- data/lib/puppet-check.rb +42 -33
- data/lib/puppet-check/cli.rb +21 -16
- data/lib/puppet-check/data_parser.rb +5 -5
- data/lib/puppet-check/puppet_parser.rb +17 -3
- data/lib/puppet-check/tasks.rb +1 -1
- data/spec/fixtures/manifests/eof_syntax.pp +4 -0
- data/spec/puppet-check/cli_spec.rb +8 -42
- data/spec/puppet-check/data_parser_spec.rb +4 -0
- data/spec/puppet-check/puppet_parser_spec.rb +9 -13
- data/spec/puppet-check/ruby_parser_spec.rb +1 -1
- data/spec/puppet-check_spec.rb +2 -2
- data/spec/system/system_spec.rb +4 -10
- metadata +27 -17
checksums.yaml
CHANGED
|
@@ -1,7 +1,7 @@
|
|
|
1
1
|
---
|
|
2
|
-
|
|
3
|
-
metadata.gz:
|
|
4
|
-
data.tar.gz:
|
|
2
|
+
SHA256:
|
|
3
|
+
metadata.gz: 5e965d79b58fb8bb6f0b3a3d01d94a451e628239abd3aeefc472dc6a8965cb59
|
|
4
|
+
data.tar.gz: 25554b24ad51443eb8b6eabee9aaed19003c20b833a4dc5b74f59db236a607aa
|
|
5
5
|
SHA512:
|
|
6
|
-
metadata.gz:
|
|
7
|
-
data.tar.gz:
|
|
6
|
+
metadata.gz: 70176578f2be7977ac92d902dd790647962b43fafd32f3a2c1f65af121d84633b8701e759d536f063dd4c692513a35d2e6ca536812626215f571bb587986e19b
|
|
7
|
+
data.tar.gz: d15e1217350f3c8ee6215d23b2a5806f451564e6b371ffd994004f53dcd49631ebd469782c4e5a025bde864949eddd73007ce053424b77435d571192a0a6b8f0
|
data/CHANGELOG.md
CHANGED
|
@@ -1,3 +1,10 @@
|
|
|
1
|
+
### 1.6.0 (Next)
|
|
2
|
+
- Minimum Ruby version increased to 2.1.
|
|
3
|
+
- Minimum Puppet version increased to 3.7.
|
|
4
|
+
- Minimum Puppet-Lint and Rubocop increased to 2.0 and 0.51.0.
|
|
5
|
+
- Correctly capturing new Puppet >= 5.4 parser validator output format.
|
|
6
|
+
- Refixing style checker error for empty hieradata.
|
|
7
|
+
|
|
1
8
|
### 1.5.1
|
|
2
9
|
- Slight cleanup and optimization.
|
|
3
10
|
- Fixed check for no spec directories during RSpec Puppet helper.
|
data/README.md
CHANGED
|
@@ -17,8 +17,6 @@ Puppet Check is a gem that provides a comprehensive, streamlined, and efficient
|
|
|
17
17
|
|
|
18
18
|
**IMPORTANT**: The current support for encrypted yaml validation is experimental. The code is blocked in the current release (the files will continue to be treated as unrecognized) and will be unblocked when the feature is finished in a future version.
|
|
19
19
|
|
|
20
|
-
Also, when most Ruby gems (both third party and standard) dropped support for 1.9.3, it became difficult for users to use Puppet Check with 1.9.3, and support for it was eventually dropped. This is now occurring again for 2.0.0 as few gems are supporting it anymore, and support for 2.0.0 will be discontinued in Puppet Check 1.6.0.
|
|
21
|
-
|
|
22
20
|
### Former Method for Code and Data Checks
|
|
23
21
|
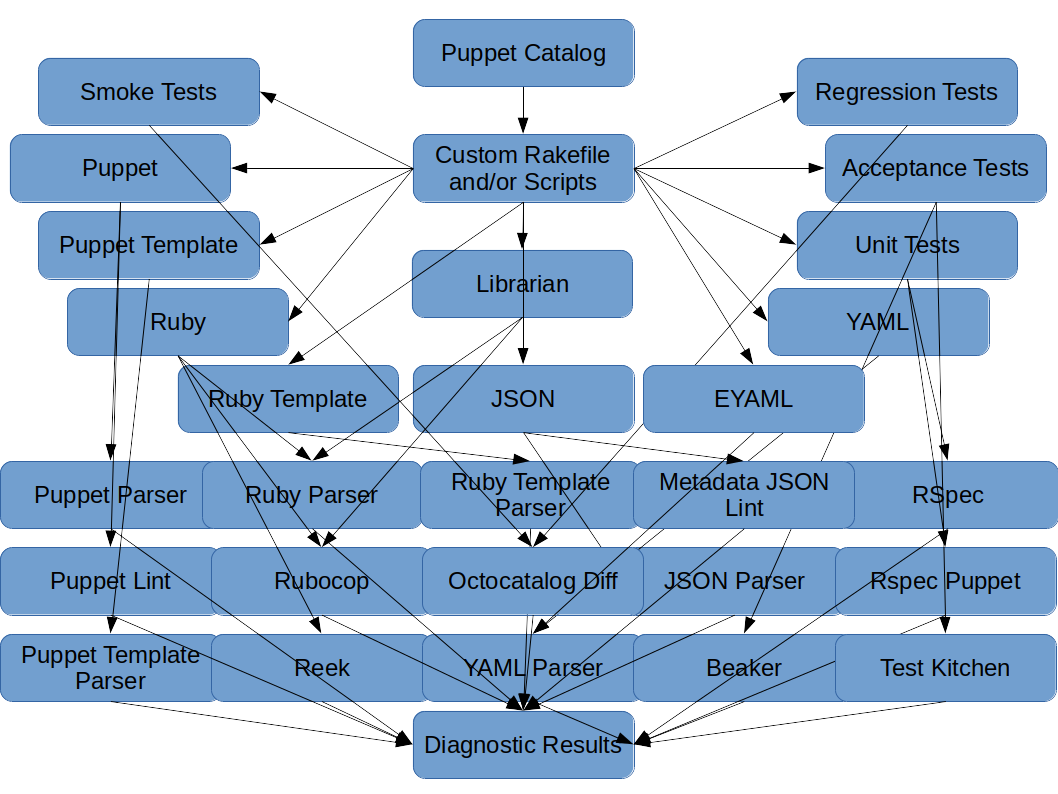
|
|
24
22
|
|
|
@@ -138,12 +136,7 @@ The following files have unrecognized formats and therefore were not processed:
|
|
|
138
136
|
It is worth nothing that there is no current development objective for Puppet Check to achieve the same advanced level of robustness for spec testing that Puppetlabs Spec Helper enables. If you are performing standard spec testing on your Puppet code and data, then Puppet Check's spec testing is a fantastic lighter and faster alternative to Puppetlabs Spec Helper. If you require advanced and intricate capabilities in your spec testing (e.g. direct interfacing to the `Puppet::Parser::Scope` API), then you will likely prefer Puppetlabs Spec Helper's spec testing in conjunction with Puppet Check's file validation.
|
|
139
137
|
|
|
140
138
|
## Usage
|
|
141
|
-
|
|
142
|
-
|
|
143
|
-
#### Ruby 2.0 and Reek/Rubocop
|
|
144
|
-
Reek dropped support for Ruby 2.0 when it went to 4.0. Since dependencies by Ruby version are allowed in Gemfiles but not gemspecs, this means that PuppetCheck installed with `bundler` will automatically pick up the correct version of Reek for your Ruby version and install it. If you are installing PuppetCheck via `gem`, then you can install reek normally with `gem` with Ruby >= 2.1, but you will need to specify `gem install reek -v 3.11` if you are using Ruby 2.0.
|
|
145
|
-
|
|
146
|
-
Similarly, RuboCop has dropped support for Ruby 2.0 at 0.51.0. Since this is a recent change, the expectation will be to automatically manage this dependency outside of Puppet Check. Only new installations on 2.0 will be affected by this.
|
|
139
|
+
Please see the [Gemspec](puppet-check.gemspec) for dependency information. All other dependencies should be fine with various versions. Puppet Check can be used with a CLI, Rake tasks, or API, from your system, rbenv, rvm, Docker, or Vagrant. Please note all interfaces (API by default, but can be modified) will ignore any directories named `fixtures` or specified paths with that directory during file checks and spec tests.
|
|
147
140
|
|
|
148
141
|
### CLI
|
|
149
142
|
```
|
|
@@ -273,20 +266,21 @@ If you are performing your Puppet testing from within a Ruby script or your own
|
|
|
273
266
|
# file checks
|
|
274
267
|
require 'puppet-check'
|
|
275
268
|
|
|
276
|
-
|
|
277
|
-
|
|
278
|
-
|
|
279
|
-
|
|
280
|
-
|
|
281
|
-
|
|
282
|
-
|
|
283
|
-
|
|
284
|
-
|
|
285
|
-
|
|
286
|
-
|
|
287
|
-
|
|
288
|
-
|
|
289
|
-
|
|
269
|
+
settings = {}
|
|
270
|
+
settings[:future_parser] = true # default false
|
|
271
|
+
settings[:fail_on_warnings] = true # default false
|
|
272
|
+
settings[:style_check] = true # default false
|
|
273
|
+
settings[:smoke_check] = true # default false
|
|
274
|
+
settings[:regression_check] = true # in progress, do not use; default false
|
|
275
|
+
settings[:public] = 'public.pem' # default nil
|
|
276
|
+
settings[:private] = 'private.pem' # default nil
|
|
277
|
+
settings[:output_format] = 'yaml' # also 'json'; default 'text'
|
|
278
|
+
settings[:octoconfig] = '$HOME/octocatalog-diff.cfg.rb' # default '.octocatalog-diff.cfg.rb'
|
|
279
|
+
settings[:octonodes] = %w(server.example.com) # default: %w(localhost.localdomain)
|
|
280
|
+
settings[:puppetlint_args] = ['--puppetlint-arg-one', '--puppetlint-arg-two'] # default []
|
|
281
|
+
settings[:rubocop_args] = ['--except', 'rubocop-arg-one,rubocop-arg-two'] # default []
|
|
282
|
+
|
|
283
|
+
PuppetCheck.new.run(settings, [dirs, files])
|
|
290
284
|
|
|
291
285
|
# rspec checks (as part of a RSpec::Core::RakeTask.new block with |task|)
|
|
292
286
|
require 'puppet-check/rspec_puppet_support'
|
|
@@ -349,19 +343,20 @@ To overcome the lack of convenient portability, you could try spinning up the Va
|
|
|
349
343
|
- 1: PuppetCheck exited with an internal exception (takes preference over other non-zero exit codes) or failed spec test(s).
|
|
350
344
|
- 2: PuppetCheck exited with one or more errors in your code and data. Alternatively, PuppetCheck exited with one or more warnings in your code and data and you specified to fail on warnings.
|
|
351
345
|
|
|
352
|
-
### Optional
|
|
346
|
+
### Optional Dependencies
|
|
353
347
|
- **rake** (gem): install this if you want to use Puppet Check with `rake` tasks in addition to the CLI.
|
|
354
348
|
- **rspec** (gem): install this if you want to use Puppet Check to execute the spec tests for your Ruby files during `rake`.
|
|
355
349
|
- **rspec-puppet** (gem): install this if you want to use Puppet Check to execute the spec tests for your Puppet files during `rake`.
|
|
356
|
-
- **octocatalog-diff** (gem): install this if you want to use Puppet Check to execute smoke or regression tests for your Puppet catalog.
|
|
350
|
+
- **octocatalog-diff** (gem): install a version `>= 1.0` of this if you want to use Puppet Check to execute smoke or regression tests for your Puppet catalog.
|
|
357
351
|
- **beaker** (gem): install this if you want to use Puppet Check to execute the Beaker acceptance tests during `rake`.
|
|
358
352
|
- **test-kitchen** (gem): install this if you want to use Puppet Check to execute the Test Kitchen acceptance tests during `rake`.
|
|
359
353
|
- **git** (pkg): install this if you want to use Puppet Check to download external module dependencies with `git` commands during RSpec Puppet testing.
|
|
360
354
|
- **mercurial** (pkg): install this if you want to use Puppet Check to download external module dependencies with `hg` commands during RSpec Puppet testing.
|
|
355
|
+
- **subversion** (pkg): install this if you want to use Puppet Check to download external module dependencies with `svn` commands during RSpec Puppet testing.
|
|
361
356
|
|
|
362
357
|
## Contributing
|
|
363
358
|
Code should pass all spec tests. New features should involve new spec tests. Adherence to Rubocop and Reek is expected where not overly onerous or where the check is of dubious cost/benefit.
|
|
364
359
|
|
|
365
360
|
A [Dockerfile](Dockerfile) is provided for easy rake testing. A [Vagrantfile](Vagrantfile) is provided for easy gem building, installation, and post-installation testing.
|
|
366
361
|
|
|
367
|
-
Please consult the
|
|
362
|
+
Please consult the GitHub Project for the current development roadmap.
|
data/lib/puppet-check.rb
CHANGED
|
@@ -8,49 +8,27 @@ class PuppetCheck
|
|
|
8
8
|
# initialize settings hash
|
|
9
9
|
@settings = {}
|
|
10
10
|
|
|
11
|
-
# initialize future parser, fail on warning, style check, and regression check bools
|
|
12
|
-
@settings[:future_parser] = false
|
|
13
|
-
@settings[:fail_on_warning] = false
|
|
14
|
-
@settings[:style_check] = false
|
|
15
|
-
@settings[:smoke_check] = false
|
|
16
|
-
@settings[:regression_check] = false
|
|
17
|
-
|
|
18
|
-
# initialize ssl keys for eyaml checks
|
|
19
|
-
@settings[:public] = nil
|
|
20
|
-
@settings[:private] = nil
|
|
21
|
-
|
|
22
|
-
# initialize output format option
|
|
23
|
-
@settings[:output_format] = 'text'
|
|
24
|
-
|
|
25
|
-
# initialize octocatalog-diff options
|
|
26
|
-
@settings[:octoconfig] = '.octocatalog-diff.cfg.rb'
|
|
27
|
-
@settings[:octonodes] = %w[localhost.localdomain]
|
|
28
|
-
|
|
29
|
-
# initialize diagnostic output arrays
|
|
30
|
-
@settings[:error_files] = []
|
|
31
|
-
@settings[:warning_files] = []
|
|
32
|
-
@settings[:clean_files] = []
|
|
33
|
-
@settings[:ignored_files] = []
|
|
34
|
-
|
|
35
|
-
# initialize style arg arrays
|
|
36
|
-
@settings[:puppetlint_args] = []
|
|
37
|
-
@settings[:rubocop_args] = []
|
|
38
|
-
|
|
39
11
|
# allow the parser methods read user options and append to the file arrays; allow CLI and tasks write to user options
|
|
40
12
|
class << self
|
|
41
13
|
attr_accessor :settings
|
|
42
14
|
end
|
|
43
15
|
|
|
44
16
|
# main runner for PuppetCheck
|
|
45
|
-
def run(paths)
|
|
17
|
+
def run(settings, paths)
|
|
18
|
+
# establish settings
|
|
19
|
+
self.class.settings = settings
|
|
20
|
+
|
|
21
|
+
# settings defaults
|
|
22
|
+
self.class.defaults
|
|
23
|
+
|
|
46
24
|
# grab all of the files to be processed
|
|
47
25
|
files = self.class.parse_paths(paths)
|
|
48
26
|
|
|
49
27
|
# parse the files
|
|
50
|
-
execute_parsers(files,
|
|
28
|
+
execute_parsers(files, settings[:future_parser], settings[:style_check], settings[:public], settings[:private], settings[:puppetlint_args], settings[:rubocop_args])
|
|
51
29
|
|
|
52
30
|
# output the diagnostic results
|
|
53
|
-
|
|
31
|
+
settings[:output_format] == 'text' ? OutputResults.text : OutputResults.markup
|
|
54
32
|
|
|
55
33
|
# progress to regression checks if no errors in file checks
|
|
56
34
|
if self.class.settings[:error_files].empty? && (!self.class.settings[:fail_on_warning] || self.class.settings[:warning_files].empty?)
|
|
@@ -63,7 +41,7 @@ class PuppetCheck
|
|
|
63
41
|
|
|
64
42
|
# perform smoke checks if there were no errors and the user desires
|
|
65
43
|
begin
|
|
66
|
-
catalog = RegressionCheck.smoke(
|
|
44
|
+
catalog = RegressionCheck.smoke(settings[:octonodes], settings[:octoconfig]) if settings[:smoke_check]
|
|
67
45
|
# smoke check failure? output message and return 2
|
|
68
46
|
rescue OctocatalogDiff::Errors::CatalogError => err
|
|
69
47
|
puts 'There was a smoke check error:'
|
|
@@ -73,7 +51,7 @@ class PuppetCheck
|
|
|
73
51
|
end
|
|
74
52
|
# perform regression checks if there were no errors and the user desires
|
|
75
53
|
# begin
|
|
76
|
-
# catalog = RegressionCheck.regression(
|
|
54
|
+
# catalog = RegressionCheck.regression(settings[:octonodes], settings[:octoconfig]) if settings[:regression_check]
|
|
77
55
|
# rescue OctocatalogDiff::Errors::CatalogError => err
|
|
78
56
|
# puts 'There was a catalog compilation error during the regression check:'
|
|
79
57
|
# puts err
|
|
@@ -89,6 +67,37 @@ class PuppetCheck
|
|
|
89
67
|
end
|
|
90
68
|
end
|
|
91
69
|
|
|
70
|
+
# establish default settings
|
|
71
|
+
def self.defaults
|
|
72
|
+
# initialize future parser, fail on warning, style check, and regression check bools
|
|
73
|
+
@settings[:future_parser] ||= false
|
|
74
|
+
@settings[:fail_on_warning] ||= false
|
|
75
|
+
@settings[:style_check] ||= false
|
|
76
|
+
@settings[:smoke_check] ||= false
|
|
77
|
+
@settings[:regression_check] ||= false
|
|
78
|
+
|
|
79
|
+
# initialize ssl keys for eyaml checks
|
|
80
|
+
@settings[:public] ||= nil
|
|
81
|
+
@settings[:private] ||= nil
|
|
82
|
+
|
|
83
|
+
# initialize output format option
|
|
84
|
+
@settings[:output_format] ||= 'text'
|
|
85
|
+
|
|
86
|
+
# initialize diagnostic output arrays
|
|
87
|
+
@settings[:error_files] = []
|
|
88
|
+
@settings[:warning_files] = []
|
|
89
|
+
@settings[:clean_files] = []
|
|
90
|
+
@settings[:ignored_files] = []
|
|
91
|
+
|
|
92
|
+
# initialize octocatalog-diff options
|
|
93
|
+
@settings[:octoconfig] ||= '.octocatalog-diff.cfg.rb'
|
|
94
|
+
@settings[:octonodes] ||= %w[localhost.localdomain]
|
|
95
|
+
|
|
96
|
+
# initialize style arg arrays
|
|
97
|
+
@settings[:puppetlint_args] ||= []
|
|
98
|
+
@settings[:rubocop_args] ||= []
|
|
99
|
+
end
|
|
100
|
+
|
|
92
101
|
# parse the paths and return the array of files
|
|
93
102
|
def self.parse_paths(paths)
|
|
94
103
|
files = []
|
data/lib/puppet-check/cli.rb
CHANGED
|
@@ -6,11 +6,11 @@ class PuppetCheck::CLI
|
|
|
6
6
|
# run method for the cli
|
|
7
7
|
def self.run(args)
|
|
8
8
|
# gather the user arguments
|
|
9
|
-
parse(args)
|
|
9
|
+
settings = parse(args)
|
|
10
10
|
raise 'puppet-check: no paths specified; try using --help' if args.empty?
|
|
11
11
|
|
|
12
12
|
# run PuppetCheck with specified paths
|
|
13
|
-
PuppetCheck.new.run(args)
|
|
13
|
+
PuppetCheck.new.run(settings, args)
|
|
14
14
|
end
|
|
15
15
|
|
|
16
16
|
# parse the user arguments
|
|
@@ -18,44 +18,49 @@ class PuppetCheck::CLI
|
|
|
18
18
|
# show help message if no args specified
|
|
19
19
|
args = %w[-h] if args.empty?
|
|
20
20
|
|
|
21
|
+
# initialize settings hash
|
|
22
|
+
settings = {}
|
|
23
|
+
|
|
21
24
|
opt_parser = OptionParser.new do |opts|
|
|
22
25
|
# usage
|
|
23
26
|
opts.banner = 'usage: puppet-check [options] paths'
|
|
24
27
|
|
|
25
28
|
# base options
|
|
26
29
|
opts.on('--version', 'Display the current version.') do
|
|
27
|
-
puts 'puppet-check 1.
|
|
30
|
+
puts 'puppet-check 1.6.0'
|
|
28
31
|
exit 0
|
|
29
32
|
end
|
|
30
33
|
|
|
31
34
|
# bool options
|
|
32
|
-
opts.on('-f', '--future', 'Enable future parser') {
|
|
33
|
-
opts.on('--fail-on-warnings', 'Fail on warnings') {
|
|
34
|
-
opts.on('-s', '--style', 'Enable style checks') {
|
|
35
|
-
opts.on('--smoke', 'Enable smoke testing') {
|
|
36
|
-
opts.on('-r', '--regression', 'Enable regression testing (in progress, do not use)') {
|
|
35
|
+
opts.on('-f', '--future', 'Enable future parser') { settings[:future_parser] = true }
|
|
36
|
+
opts.on('--fail-on-warnings', 'Fail on warnings') { settings[:fail_on_warnings] = true }
|
|
37
|
+
opts.on('-s', '--style', 'Enable style checks') { settings[:style_check] = true }
|
|
38
|
+
opts.on('--smoke', 'Enable smoke testing') { settings[:smoke_check] = true }
|
|
39
|
+
opts.on('-r', '--regression', 'Enable regression testing (in progress, do not use)') { settings[:regression_check] = true }
|
|
37
40
|
|
|
38
41
|
# ssl key options for eyaml checks
|
|
39
|
-
opts.on('--public cert.pem', String, 'Public key for EYAML checks') { |arg|
|
|
40
|
-
opts.on('--private cert.pem', String, 'Private key for EYAML checks') { |arg|
|
|
42
|
+
opts.on('--public cert.pem', String, 'Public key for EYAML checks') { |arg| settings[:public] = arg }
|
|
43
|
+
opts.on('--private cert.pem', String, 'Private key for EYAML checks') { |arg| settings[:private] = arg }
|
|
41
44
|
|
|
42
45
|
# formatting options
|
|
43
|
-
opts.on('-o', '--output format', String, 'Format for results output (default is text): text, json, or yaml') { |arg|
|
|
46
|
+
opts.on('-o', '--output format', String, 'Format for results output (default is text): text, json, or yaml') { |arg| settings[:output_format] = arg }
|
|
44
47
|
|
|
45
48
|
# octocatalog-diff options
|
|
46
|
-
opts.on('--octoconfig config_file', String, 'Octocatalog-diff configuration file to use') { |arg|
|
|
47
|
-
opts.on('-n', '--octonodes node1.example.com,node2.example.com', Array, 'Octocatalog-diff nodes to test catalog on') { |arg|
|
|
49
|
+
opts.on('--octoconfig config_file', String, 'Octocatalog-diff configuration file to use') { |arg| settings[:octoconfig] = arg }
|
|
50
|
+
opts.on('-n', '--octonodes node1.example.com,node2.example.com', Array, 'Octocatalog-diff nodes to test catalog on') { |arg| settings[:octonodes] = arg }
|
|
48
51
|
|
|
49
52
|
# arguments to style checkers
|
|
50
53
|
opts.on('--puppet-lint arg_one,arg_two', Array, 'Arguments for PuppetLint ignored checks') do |puppetlint_args|
|
|
51
|
-
|
|
54
|
+
settings[:puppetlint_args] = puppetlint_args.map { |arg| "--#{arg}" }
|
|
52
55
|
end
|
|
53
56
|
opts.on('-c', '--config file', String, 'Load PuppetLint options from file') do |file|
|
|
54
|
-
|
|
57
|
+
settings[:puppetlint_args] = File.read(file).split("\n")
|
|
55
58
|
end
|
|
56
|
-
opts.on('--rubocop arg_one,arg_two', String, 'Arguments for Rubocop disabled cops') { |arg|
|
|
59
|
+
opts.on('--rubocop arg_one,arg_two', String, 'Arguments for Rubocop disabled cops') { |arg| settings[:rubocop_args] = ['--except', arg] }
|
|
57
60
|
end
|
|
58
61
|
|
|
62
|
+
# remove atched args and return settings
|
|
59
63
|
opt_parser.parse!(args)
|
|
64
|
+
settings
|
|
60
65
|
end
|
|
61
66
|
end
|
|
@@ -16,7 +16,7 @@ class DataParser
|
|
|
16
16
|
warnings = []
|
|
17
17
|
|
|
18
18
|
# perform some rudimentary hiera checks if data exists and is hieradata
|
|
19
|
-
warnings = hiera(parsed, file)
|
|
19
|
+
warnings = hiera(parsed, file) if parsed && (File.basename(file) != 'hiera.yaml')
|
|
20
20
|
|
|
21
21
|
next PuppetCheck.settings[:warning_files].push("#{file}:\n#{warnings.join("\n")}") unless warnings.empty?
|
|
22
22
|
PuppetCheck.settings[:clean_files].push(file.to_s)
|
|
@@ -54,14 +54,14 @@ class DataParser
|
|
|
54
54
|
|
|
55
55
|
# check yaml syntax
|
|
56
56
|
begin
|
|
57
|
-
parsed = YAML.
|
|
57
|
+
parsed = YAML.load_file(decrypted)
|
|
58
58
|
rescue StandardError => err
|
|
59
59
|
PuppetCheck.settings[:error_files].push("#{file}:\n#{err.to_s.gsub("(#{file}): ", '')}")
|
|
60
60
|
else
|
|
61
61
|
warnings = []
|
|
62
62
|
|
|
63
63
|
# perform some rudimentary hiera checks if data exists and is hieradata
|
|
64
|
-
warnings = hiera(parsed, file)
|
|
64
|
+
warnings = hiera(parsed, file) if parsed
|
|
65
65
|
|
|
66
66
|
next PuppetCheck.settings[:warning_files].push("#{file}:\n#{warnings.join("\n")}") unless warnings.empty?
|
|
67
67
|
PuppetCheck.settings[:clean_files].push(file.to_s)
|
|
@@ -165,9 +165,9 @@ class DataParser
|
|
|
165
165
|
warnings.push("License identifier '#{parsed['license']}' is not in the SPDX list: http://spdx.org/licenses/")
|
|
166
166
|
end
|
|
167
167
|
# assume this is hieradata
|
|
168
|
-
|
|
168
|
+
elsif parsed
|
|
169
169
|
# perform some rudimentary hiera checks if data exists
|
|
170
|
-
warnings = hiera(parsed, file)
|
|
170
|
+
warnings = hiera(parsed, file)
|
|
171
171
|
end
|
|
172
172
|
next PuppetCheck.settings[:warning_files].push("#{file}:\n#{warnings.join("\n")}") unless warnings.empty?
|
|
173
173
|
PuppetCheck.settings[:clean_files].push(file.to_s)
|
|
@@ -21,14 +21,28 @@ class PuppetParser
|
|
|
21
21
|
Puppet::Face[:parser, :current].validate(file)
|
|
22
22
|
# this is the actual error that we need to rescue Puppet::Face from
|
|
23
23
|
rescue SystemExit
|
|
24
|
+
# puppet 5.4-5.x has a new validator output format and eof errors have fake dir env info
|
|
25
|
+
if Puppet::PUPPETVERSION.to_f >= 5.4
|
|
26
|
+
next PuppetCheck.settings[:error_files].push("#{file}:\n#{errors.map(&:to_s).join("\n").gsub(/file: #{File.absolute_path(file)}(, |\))/, '').gsub(/Could not parse.*: /, '')}")
|
|
24
27
|
# puppet 5.0-5.2 can only do one error per line and outputs fake dir env info
|
|
25
|
-
|
|
26
|
-
|
|
28
|
+
elsif Puppet::PUPPETVERSION.to_f >= 5.0 && Puppet::PUPPETVERSION.to_f < 5.3
|
|
29
|
+
next PuppetCheck.settings[:error_files].push("#{file}:\n#{errors.map(&:to_s).join("\n").gsub("#{File.absolute_path(file)}:", '').gsub(/Could not parse.*: /, '')}")
|
|
30
|
+
end
|
|
31
|
+
# puppet < 5 and 5.3 parser output style
|
|
27
32
|
next PuppetCheck.settings[:error_files].push("#{file}:\n#{errors.map(&:to_s).join("\n").gsub("#{File.absolute_path(file)}:", '')}")
|
|
28
33
|
end
|
|
29
34
|
|
|
30
35
|
# initialize warnings with output from the parser if it exists, since the output is warnings if Puppet::Face did not trigger a SystemExit
|
|
31
|
-
warnings =
|
|
36
|
+
warnings = "#{file}:"
|
|
37
|
+
unless errors.empty?
|
|
38
|
+
# puppet 5.4-5.x has a new validator output format
|
|
39
|
+
if Puppet::PUPPETVERSION.to_f >= 5.4
|
|
40
|
+
warnings << "\n#{errors.map(&:to_s).join("\n").gsub("file: #{File.absolute_path(file)}, ", '')}"
|
|
41
|
+
# puppet <= 5.3 validator output format
|
|
42
|
+
else
|
|
43
|
+
warnings << "\n#{errors.map(&:to_s).join("\n").gsub("#{File.absolute_path(file)}:", '')}"
|
|
44
|
+
end
|
|
45
|
+
end
|
|
32
46
|
Puppet::Util::Log.close_all
|
|
33
47
|
|
|
34
48
|
# check puppet style
|
data/lib/puppet-check/tasks.rb
CHANGED
|
@@ -14,7 +14,7 @@ class PuppetCheck::Tasks < ::Rake::TaskLib
|
|
|
14
14
|
namespace :puppetcheck do
|
|
15
15
|
desc 'Execute Puppet-Check file checks'
|
|
16
16
|
task :file do
|
|
17
|
-
PuppetCheck.new.run(Dir.glob('*'))
|
|
17
|
+
PuppetCheck.new.run(PuppetCheck.settings, Dir.glob('*'))
|
|
18
18
|
end
|
|
19
19
|
|
|
20
20
|
# rspec and rspec-puppet tasks
|
|
@@ -14,69 +14,35 @@ describe PuppetCheck::CLI do
|
|
|
14
14
|
end
|
|
15
15
|
|
|
16
16
|
it 'allows future parser, fail on warnings, style, smoke, and regression checks to be enabled' do
|
|
17
|
-
PuppetCheck.
|
|
18
|
-
PuppetCheck.settings[:fail_on_warnings] = false
|
|
19
|
-
PuppetCheck.settings[:style_check] = false
|
|
20
|
-
PuppetCheck.settings[:smoke_check] = false
|
|
21
|
-
PuppetCheck.settings[:regression_check] = false
|
|
22
|
-
PuppetCheck::CLI.parse(%w[-f --fail-on-warnings -s -r --smoke foo])
|
|
23
|
-
expect(PuppetCheck.settings[:future_parser]).to eql(true)
|
|
24
|
-
expect(PuppetCheck.settings[:fail_on_warnings]).to eql(true)
|
|
25
|
-
expect(PuppetCheck.settings[:style_check]).to eql(true)
|
|
26
|
-
expect(PuppetCheck.settings[:smoke_check]).to eql(true)
|
|
27
|
-
expect(PuppetCheck.settings[:regression_check]).to eql(true)
|
|
17
|
+
expect(PuppetCheck::CLI.parse(%w[-f --fail-on-warnings -s -r --smoke foo])).to include(future_parser: true, fail_on_warnings: true, style_check: true, smoke_check: true, regression_check: true)
|
|
28
18
|
end
|
|
29
19
|
|
|
30
20
|
it 'correctly parser EYAML options' do
|
|
31
|
-
PuppetCheck.
|
|
32
|
-
PuppetCheck.settings[:private] = nil
|
|
33
|
-
PuppetCheck::CLI.parse(%w[--public pub.pem --private priv.pem])
|
|
34
|
-
expect(PuppetCheck.settings[:public]).to eql('pub.pem')
|
|
35
|
-
expect(PuppetCheck.settings[:private]).to eql('priv.pem')
|
|
21
|
+
expect(PuppetCheck::CLI.parse(%w[--public pub.pem --private priv.pem])).to include(public: 'pub.pem', private: 'priv.pem')
|
|
36
22
|
end
|
|
37
23
|
|
|
38
24
|
it 'correctly parses a formatting option' do
|
|
39
|
-
PuppetCheck.
|
|
40
|
-
PuppetCheck::CLI.parse(%w[-o text])
|
|
41
|
-
expect(PuppetCheck.settings[:output_format]).to eql('text')
|
|
25
|
+
expect(PuppetCheck::CLI.parse(%w[-o text])).to include(output_format: 'text')
|
|
42
26
|
end
|
|
43
27
|
|
|
44
28
|
it 'correctly parses octocatalog-diff options' do
|
|
45
|
-
PuppetCheck.
|
|
46
|
-
PuppetCheck.settings[:octonodes] = []
|
|
47
|
-
PuppetCheck::CLI.parse(%w[--octoconfig config.cfg.rb --octonodes server1,server2])
|
|
48
|
-
expect(PuppetCheck.settings[:octoconfig]).to eql('config.cfg.rb')
|
|
49
|
-
expect(PuppetCheck.settings[:octonodes]).to eql(%w[server1 server2])
|
|
29
|
+
expect(PuppetCheck::CLI.parse(%w[--octoconfig config.cfg.rb --octonodes server1,server2])).to include(octoconfig: 'config.cfg.rb', octonodes: %w[server1 server2])
|
|
50
30
|
end
|
|
51
31
|
|
|
52
32
|
it 'correctly parses PuppetLint arguments' do
|
|
53
|
-
PuppetCheck.
|
|
54
|
-
PuppetCheck::CLI.parse(%w[--puppet-lint puppetlint-arg-one,puppetlint-arg-two foo])
|
|
55
|
-
expect(PuppetCheck.settings[:puppetlint_args]).to eql(['--puppetlint-arg-one', '--puppetlint-arg-two'])
|
|
33
|
+
expect(PuppetCheck::CLI.parse(%w[--puppet-lint puppetlint-arg-one,puppetlint-arg-two foo])).to include(puppetlint_args: ['--puppetlint-arg-one', '--puppetlint-arg-two'])
|
|
56
34
|
end
|
|
57
35
|
|
|
58
36
|
it 'correctly loads a .puppet-lint.rc' do
|
|
59
|
-
PuppetCheck.
|
|
60
|
-
PuppetCheck::CLI.parse(%W[-c #{fixtures_dir}/manifests/.puppet-lint.rc])
|
|
61
|
-
expect(PuppetCheck.settings[:puppetlint_args]).to eql(['--puppetlint-arg-one', '--puppetlint-arg-two'])
|
|
37
|
+
expect(PuppetCheck::CLI.parse(%W[-c #{fixtures_dir}/manifests/.puppet-lint.rc])).to include(puppetlint_args: ['--puppetlint-arg-one', '--puppetlint-arg-two'])
|
|
62
38
|
end
|
|
63
39
|
|
|
64
40
|
it 'correctly parses Rubocop arguments' do
|
|
65
|
-
PuppetCheck.
|
|
66
|
-
PuppetCheck::CLI.parse(%w[--rubocop rubocop-arg-one,rubocop-arg-two foo])
|
|
67
|
-
expect(PuppetCheck.settings[:rubocop_args]).to eql(['--except', 'rubocop-arg-one,rubocop-arg-two'])
|
|
41
|
+
expect(PuppetCheck::CLI.parse(%w[--rubocop rubocop-arg-one,rubocop-arg-two foo])).to include(rubocop_args: ['--except', 'rubocop-arg-one,rubocop-arg-two'])
|
|
68
42
|
end
|
|
69
43
|
|
|
70
44
|
it 'correctly parses multiple sets of arguments' do
|
|
71
|
-
PuppetCheck.
|
|
72
|
-
PuppetCheck.settings[:style_check] = false
|
|
73
|
-
PuppetCheck.settings[:puppetlint_args] = []
|
|
74
|
-
PuppetCheck.settings[:rubocop_args] = []
|
|
75
|
-
PuppetCheck::CLI.parse(%w[-s -f --puppet-lint puppetlint-arg-one,puppetlint-arg-two --rubocop rubocop-arg-one,rubocop-arg-two foo])
|
|
76
|
-
expect(PuppetCheck.settings[:future_parser]).to eql(true)
|
|
77
|
-
expect(PuppetCheck.settings[:style_check]).to eql(true)
|
|
78
|
-
expect(PuppetCheck.settings[:puppetlint_args]).to eql(['--puppetlint-arg-one', '--puppetlint-arg-two'])
|
|
79
|
-
expect(PuppetCheck.settings[:rubocop_args]).to eql(['--except', 'rubocop-arg-one,rubocop-arg-two'])
|
|
45
|
+
expect(PuppetCheck::CLI.parse(%w[-s -f --puppet-lint puppetlint-arg-one,puppetlint-arg-two --rubocop rubocop-arg-one,rubocop-arg-two foo])).to include(future_parser: true, style_check: true, puppetlint_args: ['--puppetlint-arg-one', '--puppetlint-arg-two'], rubocop_args: ['--except', 'rubocop-arg-one,rubocop-arg-two'])
|
|
80
46
|
end
|
|
81
47
|
end
|
|
82
48
|
end
|
|
@@ -31,6 +31,10 @@ describe DataParser do
|
|
|
31
31
|
|
|
32
32
|
if RUBY_VERSION.to_f >= 2.3
|
|
33
33
|
context '.eyaml' do
|
|
34
|
+
before(:each) do
|
|
35
|
+
PuppetCheck.settings[:ignored_files] = []
|
|
36
|
+
end
|
|
37
|
+
|
|
34
38
|
it 'returns a warning if a public key was not specified' do
|
|
35
39
|
expect { DataParser.eyaml(['foo.eyaml'], nil, 'private.pem') }.to output("Public X509 and/or Private RSA PKCS7 certs were not specified. EYAML checks will not be executed.\n").to_stderr
|
|
36
40
|
end
|
|
@@ -11,25 +11,21 @@ describe PuppetParser do
|
|
|
11
11
|
context '.manifest' do
|
|
12
12
|
it 'puts a bad syntax Puppet manifest in the error files array' do
|
|
13
13
|
PuppetParser.manifest([fixtures_dir + 'manifests/syntax.pp'], false, false, [])
|
|
14
|
-
#
|
|
15
|
-
if RUBY_VERSION.to_f < 2.
|
|
16
|
-
|
|
17
|
-
if Puppet::PUPPETVERSION.to_f >= 5.0 && Puppet::PUPPETVERSION.to_f < 5.3
|
|
18
|
-
expect(PuppetCheck.settings[:error_files][0]).to match(%r{^#{fixtures_dir}manifests/syntax.pp:\nSupport for ruby version.*\n.*\nThis Variable has no effect.*})
|
|
19
|
-
# puppet < 5 or >= 5.3 can do multiple errors per line
|
|
20
|
-
else
|
|
21
|
-
expect(PuppetCheck.settings[:error_files][0]).to match(%r{^#{fixtures_dir}manifests/syntax.pp:\nSupport for ruby version.*\n.*\nThis Variable has no effect.*\nIllegal variable name})
|
|
22
|
-
end
|
|
23
|
-
# no puppet deprecation warning in ruby >= 2.1 and Puppet 5.0-5.2 cannot do multiple errors per line
|
|
24
|
-
elsif Puppet::PUPPETVERSION.to_f >= 5.0 && Puppet::PUPPETVERSION.to_f < 5.3
|
|
25
|
-
expect(PuppetCheck.settings[:error_files][0]).to match(%r{^#{fixtures_dir}manifests/syntax.pp:\nThis Variable has no effect})
|
|
26
|
-
# no puppet deprecation warning in ruby >= 2.1 and puppet < 5 or >= 5.3 can do multiple errors per line
|
|
14
|
+
# dealing with annoying warning in puppet 5
|
|
15
|
+
if RUBY_VERSION.to_f < 2.3
|
|
16
|
+
expect(PuppetCheck.settings[:error_files][0]).to match(%r{^#{fixtures_dir}manifests/syntax.pp:\nSupport for ruby version.*\n.*\nThis Variable has no effect.*\nIllegal variable name})
|
|
27
17
|
else
|
|
28
18
|
expect(PuppetCheck.settings[:error_files][0]).to match(%r{^#{fixtures_dir}manifests/syntax.pp:\nThis Variable has no effect.*\nIllegal variable name})
|
|
29
19
|
end
|
|
30
20
|
expect(PuppetCheck.settings[:warning_files]).to eql([])
|
|
31
21
|
expect(PuppetCheck.settings[:clean_files]).to eql([])
|
|
32
22
|
end
|
|
23
|
+
it 'puts a bad syntax at eof Puppet manifest in the error files array' do
|
|
24
|
+
PuppetParser.manifest([fixtures_dir + 'manifests/eof_syntax.pp'], false, false, [])
|
|
25
|
+
expect(PuppetCheck.settings[:error_files][0]).to match(%r{^#{fixtures_dir}manifests/eof_syntax.pp:\nSyntax error at end of input})
|
|
26
|
+
expect(PuppetCheck.settings[:warning_files]).to eql([])
|
|
27
|
+
expect(PuppetCheck.settings[:clean_files]).to eql([])
|
|
28
|
+
end
|
|
33
29
|
it 'puts a bad parser and lint style Puppet manifest in the warning files array' do
|
|
34
30
|
PuppetParser.manifest([fixtures_dir + 'manifests/style_parser.pp'], false, true, [])
|
|
35
31
|
expect(PuppetCheck.settings[:error_files]).to eql([])
|
|
@@ -18,7 +18,7 @@ describe RubyParser do
|
|
|
18
18
|
it 'puts a bad style ruby file in the warning files array' do
|
|
19
19
|
RubyParser.ruby([fixtures_dir + 'lib/style.rb'], true, [])
|
|
20
20
|
expect(PuppetCheck.settings[:error_files]).to eql([])
|
|
21
|
-
expect(PuppetCheck.settings[:warning_files][0]).to match(%r{^#{fixtures_dir}lib/style.rb:\n.*Useless assignment.*\n.*Use the new.*\n.*Do not introduce.*\n.*Prefer single.*\n.*is a writable attribute.*\n.*Issue has no descriptive comment})
|
|
21
|
+
expect(PuppetCheck.settings[:warning_files][0]).to match(%r{^#{fixtures_dir}lib/style.rb:\n.*Useless assignment.*\n.*Use the new.*\n.*Do not introduce.*\n.*Prefer single.*\n.*Source code comment is empty.*\n.*is a writable attribute.*\n.*Issue has no descriptive comment})
|
|
22
22
|
expect(PuppetCheck.settings[:clean_files]).to eql([])
|
|
23
23
|
end
|
|
24
24
|
it 'puts a bad style ruby file in the clean files array when rubocop_args ignores its warnings' do
|
data/spec/puppet-check_spec.rb
CHANGED
|
@@ -50,12 +50,12 @@ describe PuppetCheck do
|
|
|
50
50
|
|
|
51
51
|
it 'correctly parses one directory and returns all of its files' do
|
|
52
52
|
dir.each { |file| expect(File.file?(file)).to be true }
|
|
53
|
-
expect(dir.length).to eql(
|
|
53
|
+
expect(dir.length).to eql(35)
|
|
54
54
|
end
|
|
55
55
|
|
|
56
56
|
it 'correctly parses multiple directories and returns all of their files' do
|
|
57
57
|
multi_dir.each { |file| expect(File.file?(file)).to be true }
|
|
58
|
-
expect(multi_dir.length).to eql(
|
|
58
|
+
expect(multi_dir.length).to eql(17)
|
|
59
59
|
end
|
|
60
60
|
|
|
61
61
|
it 'correctly parses three directories (one repeated) and three files (one repeated from directories and another repeated from files) and returns the unique files' do
|
data/spec/system/system_spec.rb
CHANGED
|
@@ -17,15 +17,9 @@ describe PuppetCheck do
|
|
|
17
17
|
|
|
18
18
|
expect { cli }.not_to raise_exception
|
|
19
19
|
|
|
20
|
-
expect(PuppetCheck.settings[:error_files].length).to eql(
|
|
21
|
-
|
|
22
|
-
|
|
23
|
-
expect(PuppetCheck.settings[:warning_files].length).to eql(10)
|
|
24
|
-
expect(PuppetCheck.settings[:clean_files].length).to eql(10)
|
|
25
|
-
else
|
|
26
|
-
expect(PuppetCheck.settings[:warning_files].length).to eql(9)
|
|
27
|
-
expect(PuppetCheck.settings[:clean_files].length).to eql(11)
|
|
28
|
-
end
|
|
20
|
+
expect(PuppetCheck.settings[:error_files].length).to eql(9)
|
|
21
|
+
expect(PuppetCheck.settings[:warning_files].length).to eql(9)
|
|
22
|
+
expect(PuppetCheck.settings[:clean_files].length).to eql(11)
|
|
29
23
|
expect(PuppetCheck.settings[:ignored_files].length).to eql(6)
|
|
30
24
|
|
|
31
25
|
expect(cli).to eql(2)
|
|
@@ -54,7 +48,7 @@ describe PuppetCheck do
|
|
|
54
48
|
|
|
55
49
|
expect { tasks }.not_to raise_exception
|
|
56
50
|
|
|
57
|
-
expect(PuppetCheck.settings[:error_files].length).to eql(
|
|
51
|
+
expect(PuppetCheck.settings[:error_files].length).to eql(9)
|
|
58
52
|
expect(PuppetCheck.settings[:warning_files].length).to eql(9)
|
|
59
53
|
expect(PuppetCheck.settings[:clean_files].length).to eql(11)
|
|
60
54
|
expect(PuppetCheck.settings[:ignored_files].length).to eql(6)
|
metadata
CHANGED
|
@@ -1,14 +1,14 @@
|
|
|
1
1
|
--- !ruby/object:Gem::Specification
|
|
2
2
|
name: puppet-check
|
|
3
3
|
version: !ruby/object:Gem::Version
|
|
4
|
-
version: 1.
|
|
4
|
+
version: 1.6.0
|
|
5
5
|
platform: ruby
|
|
6
6
|
authors:
|
|
7
7
|
- Matt Schuchard
|
|
8
8
|
autorequire:
|
|
9
9
|
bindir: bin
|
|
10
10
|
cert_chain: []
|
|
11
|
-
date: 2018-
|
|
11
|
+
date: 2018-08-12 00:00:00.000000000 Z
|
|
12
12
|
dependencies:
|
|
13
13
|
- !ruby/object:Gem::Dependency
|
|
14
14
|
name: puppet
|
|
@@ -16,7 +16,7 @@ dependencies:
|
|
|
16
16
|
requirements:
|
|
17
17
|
- - ">="
|
|
18
18
|
- !ruby/object:Gem::Version
|
|
19
|
-
version: '3.
|
|
19
|
+
version: '3.7'
|
|
20
20
|
- - "<"
|
|
21
21
|
- !ruby/object:Gem::Version
|
|
22
22
|
version: '6'
|
|
@@ -26,7 +26,7 @@ dependencies:
|
|
|
26
26
|
requirements:
|
|
27
27
|
- - ">="
|
|
28
28
|
- !ruby/object:Gem::Version
|
|
29
|
-
version: '3.
|
|
29
|
+
version: '3.7'
|
|
30
30
|
- - "<"
|
|
31
31
|
- !ruby/object:Gem::Version
|
|
32
32
|
version: '6'
|
|
@@ -34,36 +34,44 @@ dependencies:
|
|
|
34
34
|
name: puppet-lint
|
|
35
35
|
requirement: !ruby/object:Gem::Requirement
|
|
36
36
|
requirements:
|
|
37
|
-
- - "
|
|
38
|
-
- !ruby/object:Gem::Version
|
|
39
|
-
version: 1.1.0
|
|
40
|
-
- - "<"
|
|
37
|
+
- - "~>"
|
|
41
38
|
- !ruby/object:Gem::Version
|
|
42
|
-
version: '
|
|
39
|
+
version: '2.0'
|
|
43
40
|
type: :runtime
|
|
44
41
|
prerelease: false
|
|
45
42
|
version_requirements: !ruby/object:Gem::Requirement
|
|
46
43
|
requirements:
|
|
47
|
-
- - "
|
|
44
|
+
- - "~>"
|
|
48
45
|
- !ruby/object:Gem::Version
|
|
49
|
-
version:
|
|
50
|
-
|
|
46
|
+
version: '2.0'
|
|
47
|
+
- !ruby/object:Gem::Dependency
|
|
48
|
+
name: reek
|
|
49
|
+
requirement: !ruby/object:Gem::Requirement
|
|
50
|
+
requirements:
|
|
51
|
+
- - "~>"
|
|
52
|
+
- !ruby/object:Gem::Version
|
|
53
|
+
version: '4.0'
|
|
54
|
+
type: :runtime
|
|
55
|
+
prerelease: false
|
|
56
|
+
version_requirements: !ruby/object:Gem::Requirement
|
|
57
|
+
requirements:
|
|
58
|
+
- - "~>"
|
|
51
59
|
- !ruby/object:Gem::Version
|
|
52
|
-
version: '
|
|
60
|
+
version: '4.0'
|
|
53
61
|
- !ruby/object:Gem::Dependency
|
|
54
62
|
name: rubocop
|
|
55
63
|
requirement: !ruby/object:Gem::Requirement
|
|
56
64
|
requirements:
|
|
57
65
|
- - "~>"
|
|
58
66
|
- !ruby/object:Gem::Version
|
|
59
|
-
version: '0'
|
|
67
|
+
version: '0.51'
|
|
60
68
|
type: :runtime
|
|
61
69
|
prerelease: false
|
|
62
70
|
version_requirements: !ruby/object:Gem::Requirement
|
|
63
71
|
requirements:
|
|
64
72
|
- - "~>"
|
|
65
73
|
- !ruby/object:Gem::Version
|
|
66
|
-
version: '0'
|
|
74
|
+
version: '0.51'
|
|
67
75
|
- !ruby/object:Gem::Dependency
|
|
68
76
|
name: spdx-licenses
|
|
69
77
|
requirement: !ruby/object:Gem::Requirement
|
|
@@ -167,6 +175,7 @@ files:
|
|
|
167
175
|
- spec/fixtures/librarian_good/Puppetfile
|
|
168
176
|
- spec/fixtures/librarian_style/Puppetfile
|
|
169
177
|
- spec/fixtures/librarian_syntax/Puppetfile
|
|
178
|
+
- spec/fixtures/manifests/eof_syntax.pp
|
|
170
179
|
- spec/fixtures/manifests/good.pp
|
|
171
180
|
- spec/fixtures/manifests/style_lint.pp
|
|
172
181
|
- spec/fixtures/manifests/style_parser.pp
|
|
@@ -212,7 +221,7 @@ required_ruby_version: !ruby/object:Gem::Requirement
|
|
|
212
221
|
requirements:
|
|
213
222
|
- - ">="
|
|
214
223
|
- !ruby/object:Gem::Version
|
|
215
|
-
version: 2.
|
|
224
|
+
version: 2.1.0
|
|
216
225
|
required_rubygems_version: !ruby/object:Gem::Requirement
|
|
217
226
|
requirements:
|
|
218
227
|
- - ">="
|
|
@@ -220,7 +229,7 @@ required_rubygems_version: !ruby/object:Gem::Requirement
|
|
|
220
229
|
version: '0'
|
|
221
230
|
requirements: []
|
|
222
231
|
rubyforge_project:
|
|
223
|
-
rubygems_version: 2.
|
|
232
|
+
rubygems_version: 2.7.6
|
|
224
233
|
signing_key:
|
|
225
234
|
specification_version: 4
|
|
226
235
|
summary: A streamlined comprehensive set of checks for your entire Puppet code and
|
|
@@ -244,6 +253,7 @@ test_files:
|
|
|
244
253
|
- spec/fixtures/librarian_good/Puppetfile
|
|
245
254
|
- spec/fixtures/librarian_style/Puppetfile
|
|
246
255
|
- spec/fixtures/librarian_syntax/Puppetfile
|
|
256
|
+
- spec/fixtures/manifests/eof_syntax.pp
|
|
247
257
|
- spec/fixtures/manifests/good.pp
|
|
248
258
|
- spec/fixtures/manifests/style_lint.pp
|
|
249
259
|
- spec/fixtures/manifests/style_parser.pp
|