jekyll-cve-badge 0.0.1
This diff represents the content of publicly available package versions that have been released to one of the supported registries. The information contained in this diff is provided for informational purposes only and reflects changes between package versions as they appear in their respective public registries.
- checksums.yaml +7 -0
- data/.gitignore +11 -0
- data/Gemfile +3 -0
- data/LICENSE.txt +21 -0
- data/README.md +30 -0
- data/Rakefile +1 -0
- data/jekyll-cve-badge.gemspec +23 -0
- data/lib/jekyll-cve-badge/api-helper.rb +27 -0
- data/lib/jekyll-cve-badge/version.rb +5 -0
- data/lib/jekyll-cve-badge.rb +75 -0
- metadata +94 -0
checksums.yaml
ADDED
|
@@ -0,0 +1,7 @@
|
|
|
1
|
+
---
|
|
2
|
+
SHA256:
|
|
3
|
+
metadata.gz: e152973b1af5f5b503e255a95f0504447b2d94dc03ce3f3f6229c6a33fbccf5e
|
|
4
|
+
data.tar.gz: 4fc0f7d858597e6f8eb11c234708f7f5b435c158373aad245bc3d8ac86a8bafe
|
|
5
|
+
SHA512:
|
|
6
|
+
metadata.gz: 69aad079968893ffce9ec349b879b2c0c7156afa40cacad51d7edefec9f919a973a2f6ec8d9e1df76864ec9edefb17abeef58a1e5a774fbe9f8a7b2eaa1a68e7
|
|
7
|
+
data.tar.gz: f158849c3bda81a3d5dc5f4f04c1f585ad51e5518d79a66b603f0d67721ee016da39aa1e23aa5ab754a5d2dad027ff4805e7e54d7ff611f6dafebc12ea5cf490
|
data/.gitignore
ADDED
data/Gemfile
ADDED
data/LICENSE.txt
ADDED
|
@@ -0,0 +1,21 @@
|
|
|
1
|
+
The MIT License (MIT)
|
|
2
|
+
|
|
3
|
+
Copyright (c) 2021 Rasmus Moorats
|
|
4
|
+
|
|
5
|
+
Permission is hereby granted, free of charge, to any person obtaining a copy
|
|
6
|
+
of this software and associated documentation files (the "Software"), to deal
|
|
7
|
+
in the Software without restriction, including without limitation the rights
|
|
8
|
+
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
|
9
|
+
copies of the Software, and to permit persons to whom the Software is
|
|
10
|
+
furnished to do so, subject to the following conditions:
|
|
11
|
+
|
|
12
|
+
The above copyright notice and this permission notice shall be included in
|
|
13
|
+
all copies or substantial portions of the Software.
|
|
14
|
+
|
|
15
|
+
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
|
16
|
+
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
|
17
|
+
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
|
18
|
+
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
|
19
|
+
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
|
20
|
+
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
|
|
21
|
+
THE SOFTWARE.
|
data/README.md
ADDED
|
@@ -0,0 +1,30 @@
|
|
|
1
|
+
# Jekyll CVE badge
|
|
2
|
+
|
|
3
|
+
Generates a shields-like badge for a specified CVE. Automatically fetches the CVSS score from NVD and generates the badge accordingly.
|
|
4
|
+
|
|
5
|
+
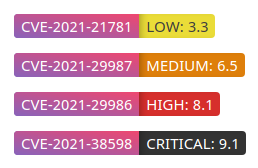
|
|
6
|
+
|
|
7
|
+
It uses CVSSv3 by default. If the CVE is old and a CVSSv3 is not available, CVSSv2 will be used. The badge itself links to the corresponding page on NVD.
|
|
8
|
+
|
|
9
|
+
### Installation and usage
|
|
10
|
+
|
|
11
|
+
Add the following to your Gemfile's jekyll_plugins group:
|
|
12
|
+
```rb
|
|
13
|
+
gem "jekyll-cve-badge", :git => "https://github.com/neonsea/jekyll-cve-badge.git"
|
|
14
|
+
```
|
|
15
|
+
|
|
16
|
+
Run `bundler install`.
|
|
17
|
+
|
|
18
|
+
You can then use the tag `cve_badge` anywhere. For example:
|
|
19
|
+
```md
|
|
20
|
+
{% cve_badge "CVE-2021-31698" %}
|
|
21
|
+
```
|
|
22
|
+
|
|
23
|
+
### Notes
|
|
24
|
+
|
|
25
|
+
* NVD's API is slow, so posts will take quite a lot longer to generate. Not much I can do here
|
|
26
|
+
* Add a `cve-badge.html` in your `_layouts` directory for custom styling. The layout is passed the params `cve_id`, `cve_severity`, and `cve_score`
|
|
27
|
+
|
|
28
|
+
### TODO
|
|
29
|
+
|
|
30
|
+
* Add flag to just add the badge with no CVSS rating
|
data/Rakefile
ADDED
|
@@ -0,0 +1 @@
|
|
|
1
|
+
require "bundler/gem_tasks"
|
|
@@ -0,0 +1,23 @@
|
|
|
1
|
+
# coding: utf-8
|
|
2
|
+
lib = File.expand_path('../lib', __FILE__)
|
|
3
|
+
$LOAD_PATH.unshift(lib) unless $LOAD_PATH.include?(lib)
|
|
4
|
+
require 'jekyll-cve-badge/version'
|
|
5
|
+
|
|
6
|
+
Gem::Specification.new do |spec|
|
|
7
|
+
spec.name = "jekyll-cve-badge"
|
|
8
|
+
spec.version = Jekyll::CVEBadge::VERSION
|
|
9
|
+
spec.authors = ["Rasmus Moorats"]
|
|
10
|
+
spec.email = ["xx@nns.ee"]
|
|
11
|
+
|
|
12
|
+
spec.summary = %q{Jekyll plugin to embed a shields-like badge for CVE IDs}
|
|
13
|
+
spec.description = %q{Jekyll plugin to embed a shields-like badge for CVE IDs}
|
|
14
|
+
spec.homepage = "https://github.com/neonsea/jekyll-cve-badge"
|
|
15
|
+
spec.license = "MIT"
|
|
16
|
+
|
|
17
|
+
spec.files = `git ls-files -z`.split("\x0").reject { |f| f.match(%r{^(test|spec|features)/}) }
|
|
18
|
+
spec.require_paths = ["lib"]
|
|
19
|
+
|
|
20
|
+
spec.add_dependency 'jekyll'
|
|
21
|
+
spec.add_development_dependency "bundler", "~> 2.2"
|
|
22
|
+
spec.add_development_dependency "rake", "~> 10.0"
|
|
23
|
+
end
|
|
@@ -0,0 +1,27 @@
|
|
|
1
|
+
module Jekyll
|
|
2
|
+
module CVEBadge
|
|
3
|
+
module APIHelper
|
|
4
|
+
|
|
5
|
+
def get_cvss_severity_score(cve_id)
|
|
6
|
+
uri = URI.parse("https://services.nvd.nist.gov/rest/json/cve/1.0/#{cve_id}")
|
|
7
|
+
|
|
8
|
+
http = Net::HTTP.new(uri.host, uri.port)
|
|
9
|
+
http.use_ssl = true
|
|
10
|
+
request = Net::HTTP::Get.new(uri.request_uri)
|
|
11
|
+
response = http.request(request)
|
|
12
|
+
|
|
13
|
+
if response.code != "200"
|
|
14
|
+
[nil, nil]
|
|
15
|
+
end
|
|
16
|
+
|
|
17
|
+
result = JSON.parse(response.body)
|
|
18
|
+
|
|
19
|
+
if result["result"]["CVE_Items"][0]["impact"]["baseMetricV3"] != nil
|
|
20
|
+
[result["result"]["CVE_Items"][0]["impact"]["baseMetricV3"]["cvssV3"]["baseSeverity"], result["result"]["CVE_Items"][0]["impact"]["baseMetricV3"]["cvssV3"]["baseScore"]]
|
|
21
|
+
else
|
|
22
|
+
[result["result"]["CVE_Items"][0]["impact"]["baseMetricV2"]["severity"], result["result"]["CVE_Items"][0]["impact"]["baseMetricV2"]["cvssV2"]["baseScore"]]
|
|
23
|
+
end
|
|
24
|
+
end
|
|
25
|
+
end
|
|
26
|
+
end
|
|
27
|
+
end
|
|
@@ -0,0 +1,75 @@
|
|
|
1
|
+
require "jekyll"
|
|
2
|
+
require "jekyll-cve-badge/api-helper"
|
|
3
|
+
require "jekyll-cve-badge/version"
|
|
4
|
+
require "json"
|
|
5
|
+
require "net/http"
|
|
6
|
+
require "uri"
|
|
7
|
+
class CVEBadge < Liquid::Tag
|
|
8
|
+
|
|
9
|
+
include Jekyll::CVEBadge::APIHelper
|
|
10
|
+
|
|
11
|
+
def initialize(tagName, content, tokens)
|
|
12
|
+
super
|
|
13
|
+
@content = content
|
|
14
|
+
end
|
|
15
|
+
|
|
16
|
+
def render(context)
|
|
17
|
+
cve_id = "#{context[@content.strip]}"
|
|
18
|
+
|
|
19
|
+
(cve_severity, cve_score) = get_cvss_severity_score(cve_id)
|
|
20
|
+
|
|
21
|
+
tmpl_path = File.join Dir.pwd, "_includes", "cve-badge.html"
|
|
22
|
+
if File.exist?(tmpl_path)
|
|
23
|
+
tmpl = File.read tmpl_path
|
|
24
|
+
site = context.registers[:site]
|
|
25
|
+
tmpl = (Liquid::Template.parse tmpl).render site.site_payload.merge!({"cve_id" => @cve_id, "cve_severity" => @cve_severity, "cve_score" => @cve_score})
|
|
26
|
+
else
|
|
27
|
+
%Q{<style>
|
|
28
|
+
.cve-container {
|
|
29
|
+
margin-bottom: 1em;
|
|
30
|
+
}
|
|
31
|
+
|
|
32
|
+
.cve-container > a {
|
|
33
|
+
border-bottom: none;
|
|
34
|
+
}
|
|
35
|
+
|
|
36
|
+
.cve-badge {
|
|
37
|
+
color: #fff;
|
|
38
|
+
padding: 2px 7px;
|
|
39
|
+
font-weight: 300;
|
|
40
|
+
font-size: 1.5rem;
|
|
41
|
+
}
|
|
42
|
+
|
|
43
|
+
.cve-id {
|
|
44
|
+
border-radius: 4px 0px 0px 4px;
|
|
45
|
+
background-color: #8963BA;
|
|
46
|
+
background-image: linear-gradient(to top right, #8963BA, #EF476F);
|
|
47
|
+
}
|
|
48
|
+
|
|
49
|
+
.cve-score {
|
|
50
|
+
border-radius: 0px 4px 4px 0px;
|
|
51
|
+
box-shadow: inset 7px 0 10px -7px rgb(0 0 0 / 0.4);
|
|
52
|
+
}
|
|
53
|
+
|
|
54
|
+
.cve-score.severity-critical {
|
|
55
|
+
background-color: #333333;
|
|
56
|
+
}
|
|
57
|
+
|
|
58
|
+
.cve-score.severity-high {
|
|
59
|
+
background-color: #d62f2c;
|
|
60
|
+
}
|
|
61
|
+
|
|
62
|
+
.cve-score.severity-medium {
|
|
63
|
+
background-color: #de7f0b;
|
|
64
|
+
}
|
|
65
|
+
|
|
66
|
+
.cve-score.severity-low {
|
|
67
|
+
background-color: #eadc38;
|
|
68
|
+
color: #3f3f3f;
|
|
69
|
+
}
|
|
70
|
+
</style><div class="cve-container"><a href="https://nvd.nist.gov/vuln/detail/#{cve_id}"><span class="cve-badge cve-id">#{cve_id}</span><span class="cve-badge cve-score severity-#{cve_severity.downcase}">#{cve_severity}: #{cve_score}</span></a></div>}
|
|
71
|
+
end
|
|
72
|
+
end
|
|
73
|
+
|
|
74
|
+
Liquid::Template.register_tag "cve_badge", self
|
|
75
|
+
end
|
metadata
ADDED
|
@@ -0,0 +1,94 @@
|
|
|
1
|
+
--- !ruby/object:Gem::Specification
|
|
2
|
+
name: jekyll-cve-badge
|
|
3
|
+
version: !ruby/object:Gem::Version
|
|
4
|
+
version: 0.0.1
|
|
5
|
+
platform: ruby
|
|
6
|
+
authors:
|
|
7
|
+
- Rasmus Moorats
|
|
8
|
+
autorequire:
|
|
9
|
+
bindir: bin
|
|
10
|
+
cert_chain: []
|
|
11
|
+
date: 2021-09-14 00:00:00.000000000 Z
|
|
12
|
+
dependencies:
|
|
13
|
+
- !ruby/object:Gem::Dependency
|
|
14
|
+
name: jekyll
|
|
15
|
+
requirement: !ruby/object:Gem::Requirement
|
|
16
|
+
requirements:
|
|
17
|
+
- - ">="
|
|
18
|
+
- !ruby/object:Gem::Version
|
|
19
|
+
version: '0'
|
|
20
|
+
type: :runtime
|
|
21
|
+
prerelease: false
|
|
22
|
+
version_requirements: !ruby/object:Gem::Requirement
|
|
23
|
+
requirements:
|
|
24
|
+
- - ">="
|
|
25
|
+
- !ruby/object:Gem::Version
|
|
26
|
+
version: '0'
|
|
27
|
+
- !ruby/object:Gem::Dependency
|
|
28
|
+
name: bundler
|
|
29
|
+
requirement: !ruby/object:Gem::Requirement
|
|
30
|
+
requirements:
|
|
31
|
+
- - "~>"
|
|
32
|
+
- !ruby/object:Gem::Version
|
|
33
|
+
version: '2.2'
|
|
34
|
+
type: :development
|
|
35
|
+
prerelease: false
|
|
36
|
+
version_requirements: !ruby/object:Gem::Requirement
|
|
37
|
+
requirements:
|
|
38
|
+
- - "~>"
|
|
39
|
+
- !ruby/object:Gem::Version
|
|
40
|
+
version: '2.2'
|
|
41
|
+
- !ruby/object:Gem::Dependency
|
|
42
|
+
name: rake
|
|
43
|
+
requirement: !ruby/object:Gem::Requirement
|
|
44
|
+
requirements:
|
|
45
|
+
- - "~>"
|
|
46
|
+
- !ruby/object:Gem::Version
|
|
47
|
+
version: '10.0'
|
|
48
|
+
type: :development
|
|
49
|
+
prerelease: false
|
|
50
|
+
version_requirements: !ruby/object:Gem::Requirement
|
|
51
|
+
requirements:
|
|
52
|
+
- - "~>"
|
|
53
|
+
- !ruby/object:Gem::Version
|
|
54
|
+
version: '10.0'
|
|
55
|
+
description: Jekyll plugin to embed a shields-like badge for CVE IDs
|
|
56
|
+
email:
|
|
57
|
+
- xx@nns.ee
|
|
58
|
+
executables: []
|
|
59
|
+
extensions: []
|
|
60
|
+
extra_rdoc_files: []
|
|
61
|
+
files:
|
|
62
|
+
- ".gitignore"
|
|
63
|
+
- Gemfile
|
|
64
|
+
- LICENSE.txt
|
|
65
|
+
- README.md
|
|
66
|
+
- Rakefile
|
|
67
|
+
- jekyll-cve-badge.gemspec
|
|
68
|
+
- lib/jekyll-cve-badge.rb
|
|
69
|
+
- lib/jekyll-cve-badge/api-helper.rb
|
|
70
|
+
- lib/jekyll-cve-badge/version.rb
|
|
71
|
+
homepage: https://github.com/neonsea/jekyll-cve-badge
|
|
72
|
+
licenses:
|
|
73
|
+
- MIT
|
|
74
|
+
metadata: {}
|
|
75
|
+
post_install_message:
|
|
76
|
+
rdoc_options: []
|
|
77
|
+
require_paths:
|
|
78
|
+
- lib
|
|
79
|
+
required_ruby_version: !ruby/object:Gem::Requirement
|
|
80
|
+
requirements:
|
|
81
|
+
- - ">="
|
|
82
|
+
- !ruby/object:Gem::Version
|
|
83
|
+
version: '0'
|
|
84
|
+
required_rubygems_version: !ruby/object:Gem::Requirement
|
|
85
|
+
requirements:
|
|
86
|
+
- - ">="
|
|
87
|
+
- !ruby/object:Gem::Version
|
|
88
|
+
version: '0'
|
|
89
|
+
requirements: []
|
|
90
|
+
rubygems_version: 3.2.5
|
|
91
|
+
signing_key:
|
|
92
|
+
specification_version: 4
|
|
93
|
+
summary: Jekyll plugin to embed a shields-like badge for CVE IDs
|
|
94
|
+
test_files: []
|